In the rapidly evolving landscape of cloud-native architectures, API gateways have emerged as critical components that serve as the primary entry point for external traffic into microservices ecosystems. As organizations increasingly adopt cloud-native approaches to application development and deployment, the security of API gateways has become paramount to overall enterprise security posture. This article examines the current threat landscape, provides comprehensive security recommendations, and outlines best practices for securing API gateways in cloud-native environments.
Modern enterprise IT systems rely heavily on application programming interfaces (APIs) for integration to support organizational business processes. The National Institute of Standards and Technology (NIST) recently released Special Publication 800-228, “Guidelines for API Protection for Cloud-Native Systems,”1 emphasizing that secure deployment of APIs is critical for overall enterprise security.
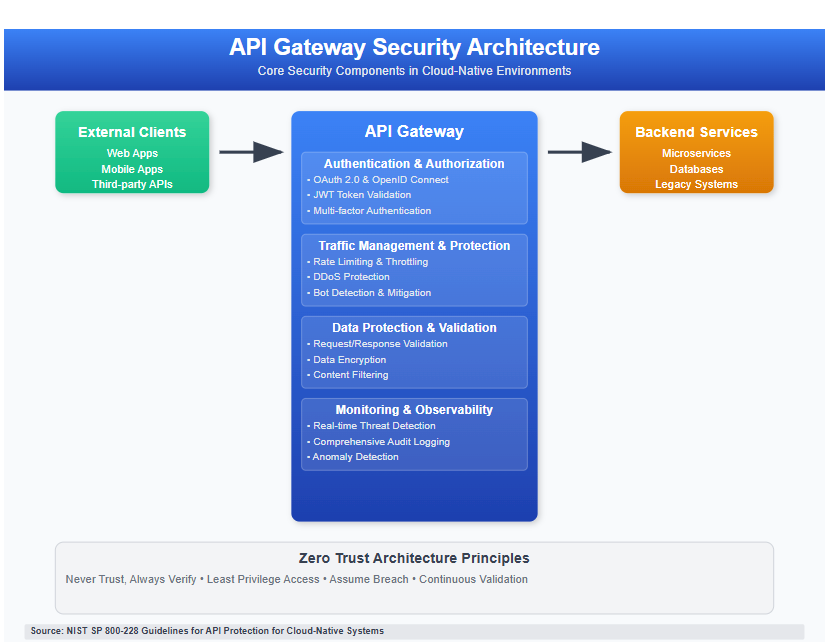
API gateways act as intermediaries between clients and backend services, functioning as reverse proxies that centralize authentication, authorization, rate limiting policies, and traffic filtering capabilities. In cloud-native architectures, these gateways become the first line of defense against potential security threats, making their proper configuration and protection essential for maintaining system integrity.
Current Threat Landscape and Statistics
OWASP API Security Top 10 (2023 Edition)
The Open Web Application Security Project (OWASP) Foundation has identified the ten most critical API security risks in their 2023 edition – OWASP Top 10 API Security Risks – 2023,2 which directly impact API gateway security:
- API1:2023 – Broken Object Level Authorization: APIs expose endpoints handling object identifiers, creating extensive attack surfaces
- API2:2023 – Broken Authentication: Incorrectly implemented authentication mechanisms allow attackers to compromise tokens
- API3:2023 – Broken Object Property Level Authorization: Combines excessive data exposure and mass assignment vulnerabilities
- API4:2023 – Unrestricted Resource Consumption: Attacks leading to denial of service or increased operational costs
- API5:2023 – Broken Function Level Authorization: Complex access control policies with unclear separation between functions
- API6:2023 – Unrestricted Access to Sensitive Business Flows: APIs vulnerable to automated abuse of business functionality
- API7:2023 – Server Side Request Forgery: Applications fetching remote resources without proper URI validation
- API8:2023 – Security Misconfiguration: Complex configurations that deviate from security best practices
- API9:2023 – Improper Inventory Management: Inadequate documentation and version control of API endpoints
- API10:2023 – Unsafe Consumption of APIs: Weaker security standards when consuming third-party APIs
A significant percentage of organizations have experienced some form of API security incident, with malicious actors increasingly targeting the core business logic of APIs rather than traditional infrastructure components.
Cloud-Native Architecture Vulnerabilities
Cloud-native environments present unique security challenges:
- Dynamic Infrastructure: Containers and microservices create ephemeral endpoints that traditional security tools struggle to monitor
- Distributed Authentication: Multiple services requiring authentication increase the attack surface
- Inter-service Communication: East-west traffic between services often lacks proper encryption and authentication
- Configuration Complexity: Kubernetes and container orchestration platforms introduce complex configuration requirements
API Gateway Security Architecture
Core Security Components
API gateways in cloud-native architectures must implement several critical security components:
- Authentication and Authorization Layer
- OAuth 2.0 and OpenID Connect integration
- JWT token validation and management
- Multi-factor authentication support
- Role-based access control (RBAC)
- Traffic Management and Protection
- Rate limiting and throttling
- DDoS protection mechanisms
- Bot detection and mitigation
- Load balancing and failover
- Data Protection and Validation
- Request and response validation
- Data encryption in transit and at rest
- Content filtering and sanitization
- Schema enforcement
- Monitoring and Observability
- Real-time threat detection
- Comprehensive audit logging
- Performance monitoring
- Anomaly detection
Microsoft Azure API Management Security Features
According to the “Recommendations to mitigate OWASP API Security Top 10 threats using API Management”3 by Microsoft, Microsoft Azure API Management provides comprehensive security controls addressing OWASP API threats:
- Authentication Integration: Native integration with Microsoft Entra ID (formerly Azure AD) for robust authentication mechanisms
- Policy Framework: Extensive policy library including validate-jwt, rate-limit-by-key, and content validation policies
- Network Security: Virtual network integration and private endpoint support
- Compliance: Built-in compliance with various security standards and frameworks
Implementation Best Practices
1. Authentication and Authorization
Broken Authentication Mitigation (API2:2023):4
- Implement Microsoft Entra ID for centralized authentication
- Use the validate-azure-ad-token policy for token validation
- Configure proper token expiration and signature validation
- Implement rate limiting to prevent brute force attacks
- Apply client IP filtering to reduce attack surface
Function Level Authorization (API5:2023):
- Protect all API endpoints with subscription keys
- Validate OAuth tokens using comprehensive policies
- Avoid wildcard API operations that create “catch-all” endpoints
- Implement network isolation using virtual networks or Private Link
2. Traffic Management and Rate Limiting
Resource Consumption Protection (API4:2023):
- Implement rate-limit-by-key policies for short-term throttling
- Use quota-by-key policies for long-term consumption control
- Apply stricter limits on sensitive endpoints (password reset, authentication)
- Configure built-in caching to reduce resource consumption
- Define appropriate timeout values for backend connections
3. Data Validation and Protection
Object Property Level Authorization (API3:2023):
- Use content validation policies with XML/JSON schemas
- Implement response filtering to remove excessive data
- Apply validate-status-code policies to block undefined error responses
- Use validate-headers policies for header compliance
- Implement GraphQL request validation with size and depth limits
Security Misconfiguration Prevention (API8:2023):
- Configure secure TLS settings (avoid TLS 1.0/1.1)
- Accept only encrypted traffic (HTTPS/WSS protocols)
- Implement proper CORS policies without wildcard usage
- Use Azure Policy to enforce configuration compliance
- Integrate with Azure Key Vault for secret management
4. Server-Side Request Forgery (SSRF) Prevention
SSRF Mitigation (API7:2023):
- Avoid using client-provided URLs in backend requests
- Implement hostname and port validation for external requests
- Configure appropriate timeouts for send-request policies
- Use private networking to restrict connectivity
- Validate and sanitize all request/response data
5. Inventory Management and Documentation
Proper Inventory Management (API9:2023):
- Use well-defined OpenAPI specifications as source for API imports
- Implement versioning strategy with maximum supported versions
- Separate environments with different API Management services
- Use Azure API Center for centralized inventory management
- Maintain up-to-date documentation through developer portals
NIST Guidelines Implementation
The NIST SP 800-228 provides specific recommendations for API gateway deployment:
Gateway as Identity Translator
API gateways must function as “identity translators,” converting diverse credential types into standardized forms for consistent system evaluation. This credential canonicalization is crucial for zero-trust implementation success.
Core NIST Recommendations:
- Deploy API gateways as intermediaries between clients and backend services
- Centralize authentication, authorization, and rate-limiting policies in one platform
- Implement traffic filtering and inspection capabilities
- Use gateways to enforce consistent security controls across all APIs
- Enable comprehensive logging and monitoring for security event correlation
Advanced Security Controls
Zero Trust Architecture Integration
Modern API gateways should implement zero trust principles:
- Never trust, always verify: Authenticate and authorize every request
- Least privilege access: Grant minimum necessary permissions
- Assume breach: Implement detection and response mechanisms
- Continuous validation: Monitor and validate ongoing sessions
Cloud-Native Security Tools Integration
Effective API gateway security requires integration with cloud-native security tools:
Microsoft Defender for APIs:
- Provides API security insights and recommendations
- Offers threat detection capabilities
- Integrates natively with Azure API Management
- Delivers real-time protection against OWASP threats
Azure Application Gateway and Web Application Firewall:
- Provides Layer 7 load balancing and SSL termination
- Implements web application firewall capabilities
- Offers DDoS protection and bot management
- Supports Microsoft_BotManagerRuleSet_1.0 for enhanced bot protection
Monitoring and Incident Response
Comprehensive Logging Strategy
Implement comprehensive logging across all API gateway components:
- Authentication events: Successful and failed authentication attempts
- Authorization decisions: Access granted or denied with reasoning
- Traffic patterns: Request volumes, sources, and destinations
- Error conditions: Application errors, timeouts, and failures
- Configuration changes: Policy updates and system modifications
Real-Time Threat Detection
Deploy real-time monitoring solutions:
- Anomaly detection: Identify unusual traffic patterns or behaviors
- Threshold alerting: Alert on rate limit violations or error rates
- Geographic analysis: Monitor for suspicious geographic patterns
- Behavioral analysis: Establish baselines and detect deviations
Compliance and Regulatory Considerations
Australian Regulatory Framework
Organizations operating in Australia must consider specific regulatory requirements:
Australian Cyber Security Centre (ACSC) Guidelines:
- Essential Eight security controls implementation
- Incident reporting requirements for notifiable data breaches
- Government security classifications and handling requirements
Australian Signals Directorate (ASD) Recommendations:
- Information Security Manual5 (ISM) compliance
- Cloud security guidance for government and critical infrastructure, such as the Cloud Security Guidance6
- Zero-trust architecture implementation guidelines
Industry Standards Compliance
ISO 27001/27002: Information security management systems and controls SOC 2 Type II: Security, availability, and confidentiality controls, PCI DSS: Payment card industry security standards,7 GDPR/Privacy Act: Data protection and privacy requirements
Emerging Threats and Future Considerations
AI and Machine Learning Security
As APIs increasingly serve AI and machine learning models:
- Prompt injection attacks: Malicious inputs designed to manipulate AI responses
- Model extraction: Attempts to reverse-engineer proprietary models
- Adversarial inputs: Crafted inputs designed to cause incorrect predictions
- Token consumption abuse: Unauthorized usage of expensive AI services
Mitigation strategies include:
- Semantic caching for AI APIs to reduce backend load
- Token limiting policies to control consumption and costs
- Comprehensive input validation and sanitization
- Rate limiting based on user identity and consumption patterns
Container and Kubernetes Security
Cloud-native deployments require specific security considerations:
- Pod security standards: Implementation of security contexts and policies
- Network policies: Microsegmentation between services
- Service mesh integration: Istio, Linkerd, or similar for secure service communication
- Admission controllers: Automated policy enforcement during deployment
Performance and Scalability Considerations
Optimization Strategies
Balancing security and performance requires careful optimization:
Caching Implementation:
- Response caching for frequently accessed data
- Authentication token caching to reduce validation overhead
- DNS caching for backend service resolution
- Certificate caching for TLS termination
Connection Management:
- Connection pooling for backend services
- HTTP/2 support for multiplexed connections
- Appropriate timeout configurations
- Circuit breaker patterns for fault tolerance
Cost Management and Optimization
Security-Performance Trade-offs
Implementing comprehensive security controls impacts performance and costs:
Resource Optimization:
- Right-sizing gateway instances based on traffic patterns
- Implementing appropriate auto-scaling policies
- Optimizing policy evaluation order for performance
- Using regional deployments to reduce latency
Cost Control Measures:
- Monitoring and alerting on API consumption costs
- Implementing quota policies to prevent cost overruns
- Regular review of security policy effectiveness
- Automated cost optimization recommendations
Conclusion
Securing API gateways in cloud-native architectures requires a comprehensive approach that addresses the evolving threat landscape while maintaining performance and usability. Organizations must implement layered security controls that address the OWASP API Security Top 10 threats while following NIST guidelines for cloud-native API protection.
Key success factors include:
- Comprehensive threat modeling based on current attack vectors
- Implementation of zero trust principles throughout the API ecosystem
- Continuous monitoring and incident response capabilities
- Regular security assessments and penetration testing
- Compliance with relevant regulatory frameworks
- Integration with cloud-native security tools and platforms
As the threat landscape continues to evolve, organizations must maintain vigilance and adapt their security postures accordingly. The investment in robust API gateway security pays dividends through reduced risk exposure, improved compliance posture, and enhanced customer trust.
References
- The National Institute of Standards and Technology (NIST). (2025). Guidelines for API Protection for Cloud-Native Systems. https://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-228.pdf ↩︎
- Open Web Application Security Project (OWASP). (2023). OWASP Top 10 API Security Risks – 2023. https://owasp.org/API-Security/editions/2023/en/0x11-t10/ ↩︎
- Microsoft. (2025). Recommendations to mitigate OWASP API Security Top 10 threats using API Management. https://learn.microsoft.com/en-us/azure/api-management/mitigate-owasp-api-threats ↩︎
- Open Worldwide Application Security Project. (2023). Broken Authentication Mitigation (API2:2023). https://owasp.org/API-Security/editions/2023/en/0xa2-broken-authentication/ ↩︎
- Australian Cyber Security Centre. (2025). Information Security Manual. Australian Signals Directorate. https://www.cyber.gov.au/resources-business-and-government/essential-cybersecurity/ism ↩︎
- Australian Cyber Security Centre. (2025). Cloud Security Guidance. Australian Signals Directorate. https://www.cyber.gov.au/resources-business-and-government/maintaining-devices-and-systems/cloud-security-guidance ↩︎
- PCI Security Standards Council. Payment card industry security standards. https://www.pcisecuritystandards.org/standards/pci-dss/ ↩︎
At Christian Sajere Cybersecurity and IT Infrastructure, we understand the critical importance of securing API gateways in today’s cloud-native world. Our specialized solutions provide comprehensive protection against evolving threats while maintaining optimal performance and compliance. Let us help you build a robust API security foundation that scales with your business.
Related Blog Posts
- Digital Forensics Fundamentals for IT Security Teams
- Securing Event-Driven Architectures: A Comprehensive Guide for Modern Organizations
- Integration of Vulnerability Management with DevOps
- Cross-Border Data Transfer: Legal Requirements
- Privacy by Design: Implementation Framework for Modern Organizations
- Security Awareness Program Design: Beyond Compliance
- Vulnerability Management for Third-Party Applications: A Critical Security Imperative


