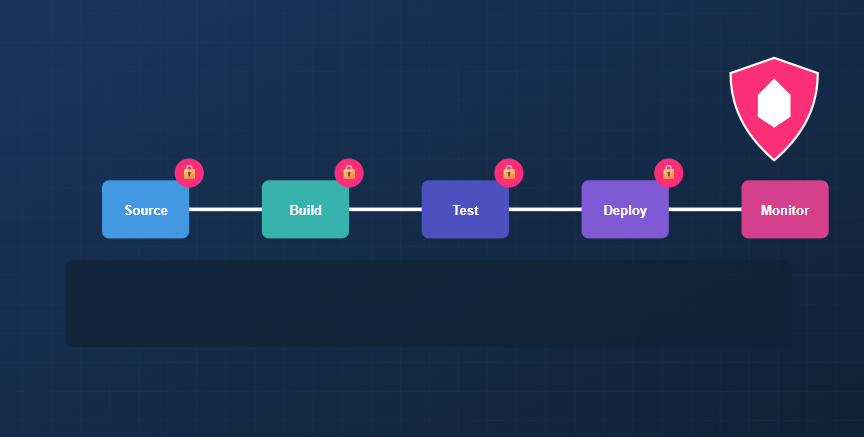
In today’s rapidly evolving digital landscape, organisations are increasingly adopting DevOps practices to accelerate software delivery and improve product quality. At the heart of these practices lies Continuous Integration and Continuous Deployment (CI/CD) pipelines, which automate the software delivery process from code commit to production deployment. However, the automation and integration capabilities that make CI/CD pipelines powerful also introduce unique security challenges. IBM’s recent discussion on software supply chain vulnerabilities, “The software supply chain was always vulnerable—JP Morgan just said it out loud”1, underscores the increasing risks, particularly in regulated industries like finance.
This article explores best practices for designing and implementing secure CI/CD pipelines, providing Australian organisations with practical strategies to protect their software development lifecycle while maintaining delivery velocity.
Understanding CI/CD Security Risks
CI/CD pipelines represent a valuable target for attackers due to their central role in software delivery. A successful attack against a CI/CD pipeline can lead to code tampering, credential theft, and the introduction of malicious code across multiple applications and environments.
Google Cloud’s “The M-Trends 2025 report”2 highlights cloud security threats, including infostealer malware and unsecured data repositories, which can impact CI/CD environments. These incidents ranged from leaked credentials to compromised dependencies, highlighting the multifaceted nature of pipeline security risks.
Common security threats to CI/CD pipelines include:
- Insecure Pipeline Configurations: Exposed secrets, excessive permissions, and lack of access controls
- Supply Chain Attacks: Compromised dependencies and malicious packages
- Infrastructure Vulnerabilities: Unpatched systems and insecure container images
- Code Injection: Malicious code introduced during build processes
- Credential Theft: Extraction of secrets and access tokens from pipeline environments
Secure CI/CD Pipeline Architecture
A secure CI/CD pipeline architecture implements security controls at every stage of the software delivery process. The following design principles should guide your implementation:
1. Isolation and Segmentation
Segregate your pipeline environments to limit the blast radius of potential compromises.
Australian Cyber Security Centre’s (ACSC) hardening guide for Windows workstations, “Hardening Microsoft Windows 10 and Windows 11 workstations,”3 emphasizes security configurations, including network segmentation and access control. Security Development Lifecycle (SDL) guidelines, each environment should be isolated with separate credentials, networks, and access controls.
Implementation strategies include:
- Creating dedicated build environments for each project or team
- Using ephemeral build environments that reset after each job
- Implementing network segmentation between pipeline stages
- Restricting communication paths between environments
2. Least Privilege Access
Apply the principle of least privilege to all pipeline components, services, and user accounts. Microsoft’s “Understanding and mitigating security risks in MCP implementations”4 shows how improper access controls can introduce vulnerabilities, emphasizing the importance of structured security policies.
Implementation strategies include:
- Creating role-based access controls for pipeline management
- Implementing just-in-time access for administrative tasks
- Restricting build job permissions to only required resources
- Regular auditing and pruning of pipeline permissions
3. Secure Configuration Management
Store configuration securely and separate from application code.
Implementation strategies include:
- Using dedicated secret management solutions
- Implementing configuration validation in pipelines
- Separating configuration from application code
- Automated scanning for hardcoded secrets
Pipeline Security Controls
1. Source Code Security
Securing the pipeline begins at the source code level. Implement the following controls:
- Branch Protection: Enforce code review and approval workflows
- Signed Commits: Require cryptographic signatures for all code changes
- Automated Security Scanning: Integrate static application security testing (SAST)
Google Cloud’s State of DevOps Report5 discusses how AI adoption and platform engineering contribute to security improvements, reinforcing the importance of structured security measures.
2. Build Process Security
The build process represents a critical security control point within the pipeline:
- Reproducible Builds: Ensure builds are deterministic and verifiable
- Dependency Scanning: Analyze dependencies for vulnerabilities and malicious code
- Integrity Verification: Generate and verify checksums for build artifacts
Microsoft’s security blog’s post, “Understanding and mitigating security risks in MCP implementations”6, shows how structured security controls can mitigate vulnerabilities, reinforcing the importance of comprehensive security measures.
3. Deployment Security
Secure deployment practices ensure that only authorized and verified code reaches production:
- Deployment Approval Gates: Require explicit approval for production deployments
- Immutable Infrastructure: Deploy immutable artifacts that cannot be modified after creation
- Progressive Deployment Strategies: Use canary releases and blue-green deployments
Implementing Security Testing in CI/CD
A comprehensive security testing strategy should be integrated throughout the CI/CD pipeline:
1. Static Application Security Testing (SAST)
SAST tools analyze source code for security vulnerabilities without executing the application.
Implementation recommendations:
- Run SAST tools on every code commit
- Integrate SAST results into developer workflows
- Establish baseline security requirements for all code
2. Dynamic Application Security Testing (DAST)
DAST tools test running applications by simulating real-world attacks.
Implementation recommendations:
- Implement DAST in staging environments
- Automate vulnerability scanning for all web interfaces
- Include API security testing in DAST workflows
3. Software Composition Analysis (SCA)
SCA tools identify and analyze open-source components used in applications.
Implementation recommendations:
- Scan all dependencies for known vulnerabilities
- Enforce policies for dependency freshness and security
- Integrate SCA into build approval processes
Monitoring and Incident Response
Continuous monitoring is essential for detecting and responding to security incidents in CI/CD pipelines:
1. Comprehensive Logging
Implement detailed logging across all pipeline components.
Implementation recommendations:
- Log all pipeline activities and access events
- Centralize logs in a secure, immutable storage system
- Establish baseline activity patterns for anomaly detection
2. Real-time Monitoring
Monitor pipeline activities to detect anomalous behavior that might indicate compromise. The Information Systems Audit and Control Association’s (ISACA) “The Never-ending Quest: Why Continuous Monitoring is Crucial for Cybersecurity”7 emphasizes the importance of proactive threat detection, highlighting how continuous monitoring helps organizations identify vulnerabilities before they escalate into security breaches.
Implementation recommendations:
- Monitor for unauthorized configuration changes
- Implement alerts for unusual build patterns or artifacts
- Track resource utilization for anomaly detection
3. Incident Response Planning
Develop specific incident response procedures for CI/CD pipeline compromises.
Implementation recommendations:
- Create playbooks for common pipeline compromise scenarios
- Regularly practice pipeline recovery procedures
- Establish clear roles and responsibilities for incident response
Compliance and Governance
Maintaining compliance while implementing CI/CD requires a structured governance approach:
1. Pipeline Policy Enforcement
Implement automated policy enforcement throughout the pipeline.
Implementation recommendations:
- Create pipeline-specific security policies
- Implement automated compliance verification
- Establish clear remediation paths for policy violations
2. Audit and Traceability
Maintain comprehensive audit trails for all pipeline activities.
Implementation recommendations:
- Record all changes to pipeline configuration
- Maintain artifact provenance information
- Implement tamper-evident logging systems
Conclusion
Secure CI/CD pipelines are essential for modern software development, enabling organizations to deliver at velocity while maintaining robust security posture. By implementing the architectural principles and security controls outlined in this article, Australian organizations can protect their software supply chain against increasingly sophisticated threats.
The research is clear: organizations that implement comprehensive CI/CD security measures experience fewer security incidents, detect issues faster, and recover more quickly than those that do not. As Christian Sajere Cybersecurity and IT Infrastructure continues to support clients in their digital transformation journeys, secure CI/CD implementation should remain a cornerstone of your security strategy.
References
- IBM, “The software supply chain was always vulnerable—JP Morgan just said it out loud”, 2025 https://www.ibm.com/think/news/jp-morgan-software-security ↩︎
- Google Cloud, “The M-Trends 2025 report”, 2025 https://services.google.com/fh/files/misc/m-trends-2025-en.pdf ↩︎
- Australian Cyber Security Centre’s (ACSC), “Hardening Microsoft Windows 10 and Windows 11 workstations,” 2024 https://www.cyber.gov.au/resources-business-and-government/maintaining-devices-and-systems/system-hardening-and-administration/system-hardening/hardening-microsoft-windows-10-and-windows-11-workstations ↩︎
- Microsoft, “Understanding and mitigating security risks in MCP implementations”, 2025 https://techcommunity.microsoft.com/blog/microsoft-security-blog/understanding-and-mitigating-security-risks-in-mcp-implementations/4404667 ↩︎
- Google Cloud, “State of DevOps Report,” 2024 https://cloud.google.com/devops/state-of-devops?hl=en ↩︎
- Microsoft, “Understanding and mitigating security risks in MCP implementations”, 2025 https://techcommunity.microsoft.com/blog/microsoft-security-blog/understanding-and-mitigating-security-risks-in-mcp-implementations/4404667 ↩︎
- Information Systems Audit and Control Association (ISACA), “The Never-ending Quest: Why Continuous Monitoring is Crucial for Cybersecurity”, 2024
↩︎
At Christian Sajere Cybersecurity and IT Infrastructure, we prioritize security in your CI/CD pipelines. Our expert solutions help design and implement resilient pipelines that safeguard your code, automate compliance, and enhance deployment efficiency. Stay ahead of threats and innovate with confidence. Let us fortify your software development lifecycle with seamless, secure integration.
Related Blog Posts
- Multi-Factor Authentication: Comparing Different Methods
- Secrets Management in DevOps Environments: Securing the Modern Software Development Lifecycle
- Zero Trust for Remote Work: Practical Implementation
- DevSecOps for Cloud: Integrating Security into CI/CD
- Customer Identity and Access Management (CIAM): The Competitive Edge for Australian Businesses
- Infrastructure as Code Security Testing: Securing the Foundation of Modern IT
- Measuring DevSecOps Success: Metrics and KPIs