Introduction
In today’s rapidly evolving digital landscape, the marriage of development and operations — DevOps — has revolutionized how organizations build, deploy, and maintain software. This integration has significantly accelerated deployment cycles, with Elite performers deploying on demand (multiple times per day) and having about 182× more deployments per year than low performers according to Google’s “2023 State of DevOps Report: Culture is everything”1. However, this velocity introduces substantial security challenges, particularly in secrets management — the practice of securing sensitive information such as API keys, database credentials, certificates, and authentication tokens.
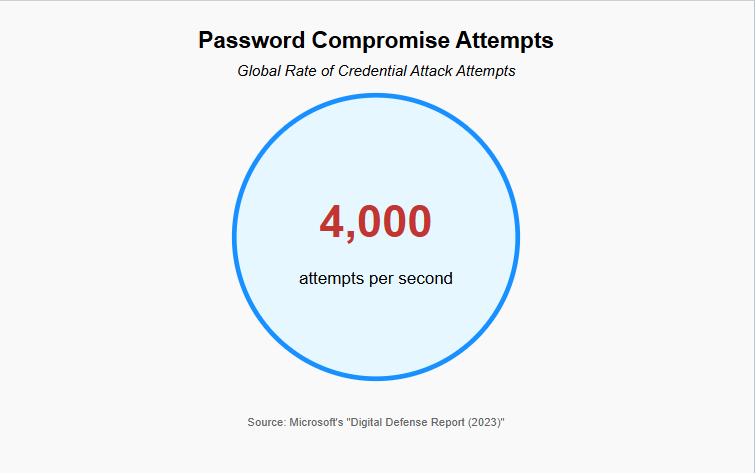
Cybersecurity threats continue to evolve, with compromised credentials emerging as a leading cause of security breaches worldwide. Reports from both the Australian Cyber Security Centre (ACSC) and Microsoft highlight the alarming role that credential theft and mismanagement play in cyber incidents. According to the ACSC’s “Annual Cyber Threat Report (2023-2024)”2, a significant percentage of data breaches in Australia involved compromised credentials. Similarly, Microsoft’s “Digital Defense Report (2023)”3 underscores the surge in credential-related attacks, revealing that attempted password compromises now occur at a rate of 4,000 per second globally. This reinforces the notion that identity-based cyber threats are among the most pressing concerns for organizations today. In DevOps environments, where automated processes require regular access to these secrets, the risk of exposure increases exponentially.
This article explores comprehensive strategies, tools, and best practices for effective secrets management in DevOps environments, focusing on approaches recommended by leading technology providers and cybersecurity authorities.
The Secrets Management Challenge in DevOps
DevOps environments present unique challenges for secrets management due to several factors:
- Automation Intensity: Continuous integration and deployment pipelines require frequent, non-interactive access to secrets.
- Infrastructure as Code (IaC): When infrastructure is defined as code, securing references to secrets within this code becomes critical.
- Container Proliferation: The widespread use of containers requires secrets to be securely distributed across ephemeral environments.
- Multi-Cloud Deployments: Organizations leveraging multiple cloud providers face increased complexity in managing secrets across heterogeneous environments.
- Developer Experience: Security controls must balance protection with developer productivity.
The IBM Security “X-Force Threat Intelligence Index”4 highlight the risks associated with improperly managed credentials and secrets in cloud environments.
Additionally, IBM’s “Cloud Threat Landscape 2023 Report”5 emphasizes that over 35% of cloud security incidents stemmed from attackers using valid, compromised credentials. This suggests that credential mismanagement remains a significant security concern.
Core Principles of Effective Secrets Management
1. Centralization
Centralized secrets management provides a single source of truth, facilitating audit, rotation, and access control. According to Microsoft’s “Insider Risk Management empowering risky AI usage visibility and security investigations“6, reports do emphasize the importance of centralized secrets management in reducing security risks. Insider risk management and adaptive protection strategies are frequently highlighted as key measures to mitigate credential-related incidents
2. Encryption
All secrets should be encrypted at rest and in transit using strong algorithms. The Australian Signals Directorate recommends AES-256 for symmetric encryption and RSA-2048 or higher for asymmetric encryption (ASD, 2023).
3. Least Privilege
Access to secrets should follow the principle of least privilege, where users and systems are granted only the minimum permissions necessary to perform their functions. Google Cloud emphasize the importance of least privilege access in reducing security risks, particularly in cloud environments. Their security reports highlight how restricting access to only necessary permissions helps minimize potential attack vectors.
4. Rotation
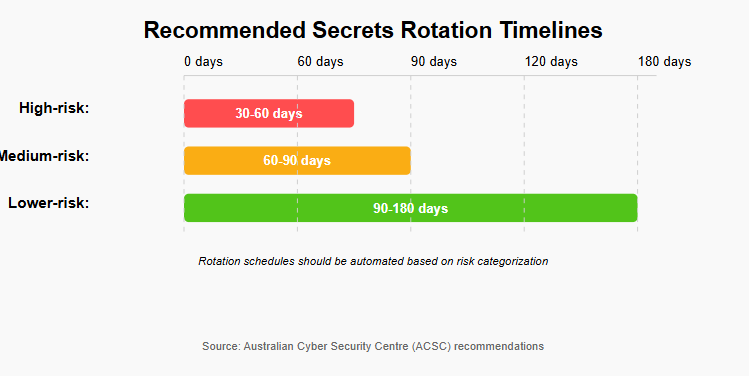
Regular rotation of secrets limits the damage potential of compromised credentials. The ACSC recommends automated rotation cycles based on risk categorization:
- High-risk environments: 30-60 days
- Medium-risk environments: 60-90 days
- Lower-risk environments: 90-180 days
5. Auditability
All secrets access should be logged and monitored, creating an audit trail that can detect unauthorized access attempts. cybersecurity studies, such as the Audit Office of New South Wales’ “NSW Audit Office’s report”7 on universities often emphasize the importance of comprehensive secrets access logging in detecting potential compromises more efficiently.
Access logging helps organizations track unauthorized access attempts, identify anomalies, and respond to security threats faster.
Implementing Secrets Management in DevOps
Secrets Management Tools and Platforms
Several enterprise-grade tools have emerged to address DevOps secrets management:
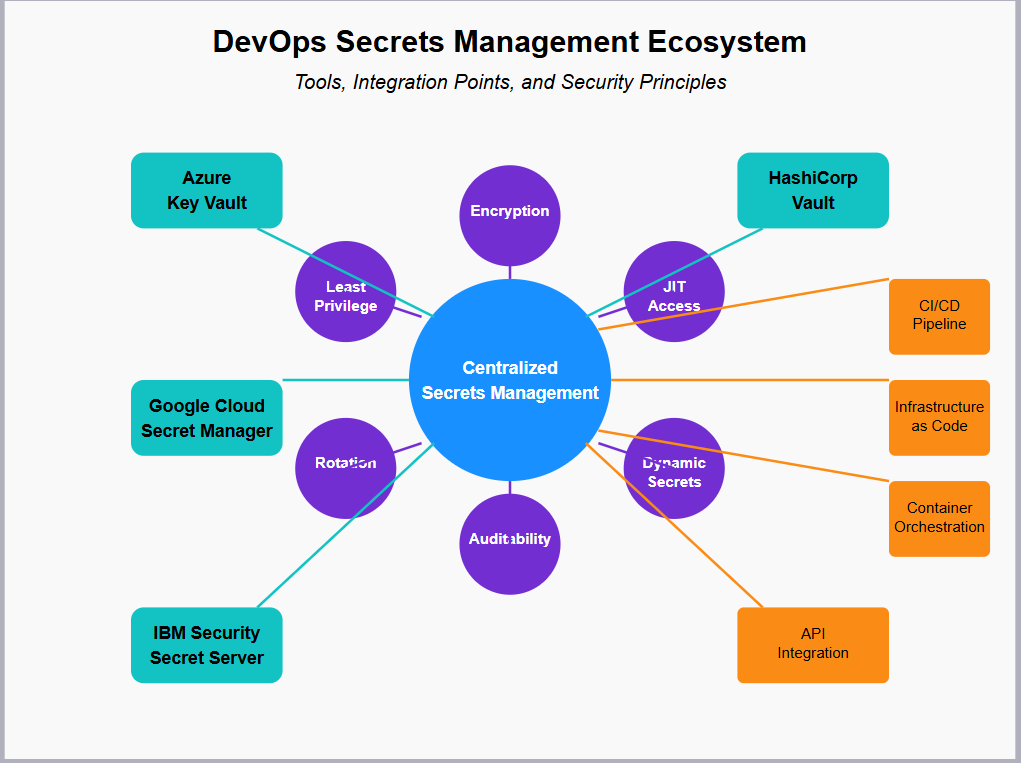
- Azure Key Vault: Microsoft’s solution for storing and controlling access to secrets, providing hardware security module (HSM) backing and tight integration with Azure services.
- Google Cloud Secret Manager: Provides central management for API keys, passwords, certificates, and other sensitive data with fine-grained access control.
- IBM Security Secret Server: Offers privileged access management capabilities alongside secrets management, with features specifically designed for hybrid and multi-cloud environments.
- Open-source alternatives: HashiCorp Vault is widely recognized as a leading open-source solution for secrets management in DevOps environments
Integration Patterns
Effective secrets management requires integration across the entire DevOps pipeline:
- CI/CD Pipeline Integration: Modern CI/CD platforms support native integration with secrets management tools.
- Infrastructure as Code: IaC tools should reference secrets stored in vaults rather than including them in templates, even as encrypted values. Microsoft’s documentation “Plan your deployment and release”8, on safe deployment practices and release management, highlights the importance of resolving configurations at deployment time to enhance security and flexibility
- Container Orchestration: Kubernetes offers native secrets management capabilities, although the ACSC recommends augmenting these with external vaults for enhanced security.
- API Integration: Applications should retrieve secrets at runtime through secure API calls rather than storing them in configuration files or environment variables.
Advanced Security Controls
Beyond basic secrets management, organizations should implement additional controls:
1. Dynamic Secrets
Rather than static credentials, dynamic secrets are generated on-demand and short-lived.
2. Just-in-Time Access
Providing time-limited access to secrets only when needed significantly reduces the exposure window.
3. Secret Detection in Source Code
Implementing automated scanning tools to detect accidentally committed secrets in code repositories is essential. Microsoft’s Advanced Security Code Scanning tools, including GitHub Advanced Security, are designed to detect exposed secrets in repositories. Research on secret detection tools titled “A Comparative Study of Software Secrets Reporting by Secret Detection Tools”9 by Setu Kumar Basak, Jamison Cox, Bradley Reaves and Laurie Williams of North Carolina State University, USA, suggests that many organizations uncover security vulnerabilities soon after implementing automated scanning solutions.
4. Secrets Rotation on Suspected Compromise
The ACSC recommends immediate rotation of all potentially affected secrets when compromise is suspected, regardless of regular rotation schedules. They emphasize the importance of rapid incident response and secrets rotation in mitigating security breaches. Their “The Commonwealth Cybersecurity Posture in 2022”10 highlight how timely security actions can significantly reduce the impact of cyber incidents.
Organizational Best Practices
1. Security Education and Training
Developer education about secrets management is crucial. Security awareness training has been shown to significantly improve an organization’s ability to detect and mitigate threats. The Journal of Knowledge Learning and Science Technology’s “Employee Cybersecurity Awareness Training Programs Customized For Sme Contexts To Reduce Human-Error Related Security Incidents”11 suggest that companies investing in cybersecurity training experience fewer security breaches and enhanced risk management.
2. Clear Policies and Standards
Establish organizational standards for secrets management that define:
- What constitutes a secret
- Required protection methods
- Rotation policies
- Emergency procedures
3. Automated Compliance Verification
Implement automated checks to verify compliance with secrets management policies. The ASD recommends continuous monitoring rather than point-in-time assessments (ASD, 2023).
4. Regular Security Assessments
Conduct regular assessments of secrets management practices, including penetration testing and code reviews.
Future Trends in Secrets Management
1. Zero Trust Architecture
The adoption of zero trust principles is reshaping secrets management, with a focus on continuous verification rather than perimeter-based security.
2. Quantum-Resistant Encryption
As quantum computing advances, encryption algorithms used to protect secrets will need to evolve. The ASD has begun recommending organizations prepare for post-quantum cryptography by implementing crypto-agility in their secrets management solutions.
3. AI-Powered Secrets Management
Artificial intelligence is being applied to detect anomalous access patterns and potential compromise of secrets.
Australian Regulatory Considerations
Australian organizations must consider several regulatory frameworks when implementing secrets management:
- Privacy Act and Notifiable Data Breaches (NDB) scheme: Requires notification of breaches involving access credentials that could lead to serious harm.
- Essential Eight Maturity Model: The ASD’s Essential Eight includes several controls directly related to secrets management, particularly in the areas of privileged access management and multi-factor authentication.
- Critical Infrastructure Security: Organizations designated as critical infrastructure must implement enhanced security controls for secrets management under the Security of Critical Infrastructure Act 2018.
Conclusion
Effective secrets management in DevOps environments requires a comprehensive approach that balances security controls with operational efficiency. By implementing centralized management, encryption, least privilege, regular rotation, and robust audit capabilities, organizations can significantly reduce the risk of breaches while maintaining the velocity that makes DevOps valuable.
The statistics are clear: organizations that implement comprehensive secrets management experience fewer breaches, detect potential compromises faster, and recover more quickly when incidents do occur. As DevOps practices continue to evolve, secrets management will remain a critical security control deserving of focused attention and investment.
For Australian organizations, particularly those in regulated industries or designated as critical infrastructure, implementing robust secrets management is not merely a security best practice but increasingly a compliance requirement. By adopting the approaches outlined in this article, organizations can build secure DevOps environments that protect sensitive information while enabling rapid innovation.
References
- Google, “2023 State of DevOps Report: Culture is everything”, 2023 https://cloud.google.com/blog/products/devops-sre/announcing-the-2023-state-of-devops-report ↩︎
- Australian Cyber Security Centre (ACSC), “Annual Cyber Threat Report (2023-2024)”, https://www.cyber.gov.au/about-us/view-all-content/reports-and-statistics/annual-cyber-threat-report-2023-2024 ↩︎
- Microsoft, “Digital Defense Report (2023)”, 2023 https://www.microsoft.com/en-us/security/security-insider/microsoft-digital-defense-report-2023 ↩︎
- IBM, “X-Force Threat Intelligence Index”, 2023 https://secure-iss.com/wp-content/uploads/2023/02/IBM-Security-X-Force-Threat-Intelligence-Index-2023.pdf ↩︎
- IBM, “Cloud Threat Landscape 2023 Report”, 2023 https://community.ibm.com/community/user/blogs/sarah-dudley/2023/09/13/x-force-cloud-threat-landscape-2023 ↩︎
- Microsoft, “Insider Risk Management empowering risky AI usage visibility and security investigations“, 2024 https://techcommunity.microsoft.com/blog/microsoft-security-blog/insider-risk-management-empowering-risky-ai-usage-visibility-and-security-invest/4298246 ↩︎
- Audit Office of New South Wales, “NSW Audit Office’s report”, 2022 https://www.audit.nsw.gov.au/our-work/reports/universities-2022 ↩︎
- Microsoft, “Plan your deployment and release”, 2024 https://learn.microsoft.com/en-us/dynamics365/guidance/implementation-guide/implementation-strategy-define-strategy-deployment-release ↩︎
- Setu K. B., et al of North Carolina State University, USA “A Comparative Study of Software Secrets Reporting by Secret Detection Tools”, 2023 https://arxiv.org/pdf/2307.00714 ↩︎
- Australian Cyber Security Centre (ACSC), “The Commonwealth Cybersecurity Posture in 2022”, 2022 https://www.cyber.gov.au/about-us/view-all-content/reports-and-statistics/commonwealth-cyber-security-posture-2022 ↩︎
- The Journal of Knowledge Learning and Science Technology, “Employee Cybersecurity Awareness Training Programs Customized For Sme Contexts To Reduce Human-Error Related Security Incidents”, 2024 https://jklst.org/index.php/home/article/view/276 ↩︎
At Christian Sajere Cybersecurity and IT Infrastructure, we understand the vital role of secrets management in modern DevOps environments. Our automated solutions ensure secure handling of sensitive credentials, API keys, and certificates throughout the software development lifecycle. By implementing robust security practices, we help organizations mitigate risks, streamline operations, and safeguard critical assets. Stay ahead with a seamless approach to securing your DevOps workflows.
Related Blog Posts
- Securing Microsoft 365 Email Environments: A Comprehensive Guide
- Crisis Communication During Security Incidents: A Strategic Approach
- Building a Security Operations Center (SOC): Key Components
- Implementing Single Sign-On: Pros, Cons, and Best Practices
- Backup and Recovery: Building Resilience Against Ransomware
- Continuous Compliance Monitoring Through Automation
- Comprehensive Security for Remote Workforces: Safeguarding the Distributed Enterprise


