Introduction
In an era where digital threats continuously evolve in sophistication, robust security measures are essential for organizations and individuals alike. Multi-Factor Authentication (MFA) has emerged as a critical defense mechanism against unauthorized access attempts, significantly reducing the risk of account compromise. This article examines the various MFA methods available today, comparing their strengths, limitations, implementation considerations, and overall effectiveness in the contemporary threat landscape.
Recent statistics from Microsoft’s “One simple action you can take to prevent 99.9 percent of attacks on your accounts”1 reveal that MFA can block over 99.9% of account compromise attacks. Despite this remarkable effectiveness, adoption rates remain suboptimal across many sectors, leaving organizations vulnerable to preventable security breaches. As cyber threats grow increasingly sophisticated, understanding the nuances of different MFA approaches becomes crucial for making informed security decisions.
Understanding Multi-Factor Authentication
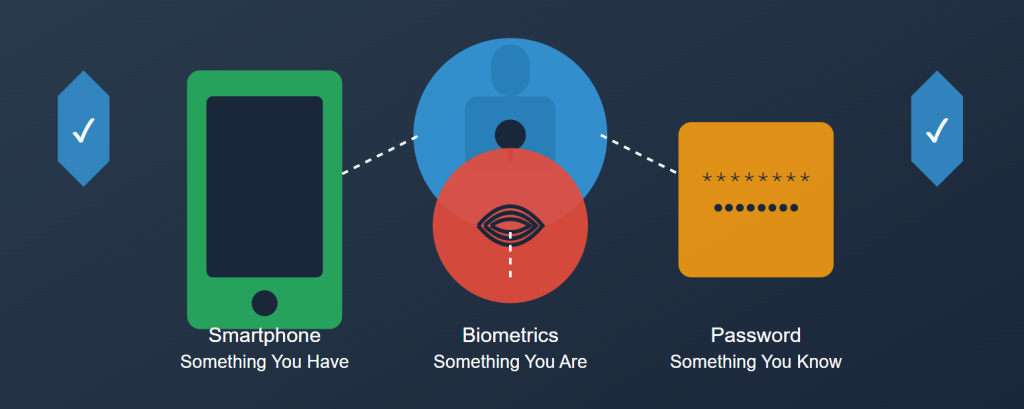
Multi-Factor Authentication strengthens security by requiring users to verify their identity through multiple validation methods. These methods typically fall into three categories:
- Something you know (knowledge factors): Passwords, PINs, security questions
- Something you have (possession factors): Mobile devices, security tokens, smart cards
- Something you are (inherence factors): Biometrics like fingerprints, facial recognition, voice patterns
The fundamental principle behind MFA is that even if attackers compromise one authentication factor (such as a password), they would still need to overcome additional verification layers to gain access. This significantly increases the difficulty of unauthorized access attempts.
Comparing MFA Methods
1. Mobile-Based Authentication
SMS-Based Authentication
SMS-based verification sends one-time codes to users’ mobile phones. While widespread and easily implemented, this method has notable security vulnerabilities.
Strengths:
- Familiar to most users
- No additional hardware required
- Widely supported across platforms
Limitations:
- Vulnerable to SIM swapping attacks
- Subject to SMS interception
- Dependent on mobile network availability
According to the Australian Cyber Security Centre’s (ACSC) “Implementing multi-factor authentication”2, SMS-based authentication should not be considered the most secure MFA option due to its susceptibility to interception. While better than no MFA at all, organizations with high-security requirements should implement stronger alternatives.
Authenticator Apps
Authenticator applications generate time-based one-time passwords (TOTPs) directly on users’ devices without requiring network connectivity or SMS messages.
Strengths:
- Not vulnerable to SMS interception
- Functions without cellular connectivity
- More resistant to phishing attacks
Limitations:
- Requires smartphone and app installation
- Device loss can create access complications
- Some implementation complexity for organizations
Research from Google Security Blog’s “New research: How effective is basic account hygiene at preventing hijacking”3 indicates that on-device prompts through authenticator apps blocked 100% of automated bots, 99% of bulk phishing attacks, and 90% of targeted attacks in their studies.
2. Hardware-Based Authentication
Security Keys
Physical security keys like FIDO U2F or FIDO2/WebAuthn compatible devices provide strong protection against phishing and man-in-the-middle attacks.
Strengths:
- Extremely resistant to phishing attacks
- No reliance on mobile networks
- Simple user experience (just plug in and tap)
Limitations:
- Additional cost for hardware purchase
- Risk of physical loss
- Limited adoption in some environments
Google reports that only a security key can stop the cleverest of phishing attacks, per their “Security keys and zero trust”4. This demonstrates the exceptional security provided by hardware-based authentication methods.
Smart Cards
Smart cards containing embedded microprocessors store cryptographic keys and perform authentication operations when inserted into compatible readers.
Strengths:
- Well-established in high-security environments
- Strong cryptographic capabilities
- Physical possession requirement
Limitations:
- Requires card readers/infrastructure
- Higher implementation and maintenance costs
- Less convenient than some alternatives
“Lightweight three-factor authentication and key agreement protocol for internet-integrated wireless sensor networks”5, published in the Institute of Electrical and Electronics Engineers (IEEE) Access, on smart card authentication highlights its effectiveness in reducing account compromise incidents compared to password-only environments.
3. Biometric Authentication
Fingerprint Recognition
Fingerprint authentication has become ubiquitous on mobile devices and increasingly common in enterprise environments.
Strengths:
- Convenient and quick verification
- Cannot be forgotten (unlike passwords)
- Difficult to duplicate precisely
Limitations:
- False accept/reject rates create usability issues
- Permanent credential that cannot be changed if compromised
- Varying quality across different implementations
Facial Recognition
Facial recognition systems analyze facial features to verify identity, with advanced systems using 3D mapping to enhance security.
Strengths:
- Contactless authentication
- Increasingly accurate with technological advances
- Natural and intuitive user experience
Limitations:
- Variable performance in different lighting conditions
- Privacy concerns in some implementations
- Potential for presentation attacks (e.g., photos)
4. Behavioral Biometrics and Contextual Authentication
Behavioral Biometrics
This emerging approach analyzes patterns in user behavior, such as typing rhythms, mouse movements, or gait analysis.
Strengths:
- Continuous authentication rather than point-in-time
- Can operate passively without user intervention
- Difficult for attackers to mimic precisely
Limitations:
- Still maturing technologically
- Privacy implications of continuous monitoring
- Potential for false rejections with behavior changes
Risk-Based/Contextual Authentication
These systems adapt authentication requirements based on risk assessment of the login attempt, considering factors like location, device, time, and behavior patterns.
Strengths:
- Balances security and convenience
- Adapts to changing threat conditions
- Minimizes friction for low-risk scenarios
Limitations:
- Complex implementation and tuning
- Potential for false assessments
- Requires substantial data for effective operation
Microsoft’s research, “How effective is multifactor authentication at deterring cyberattacks?”6 emphasizes that risk-based authentication — which adapts security measures based on user behavior and risk signals — can significantly reduce account compromises compared to standard MFA alone.
Effectiveness Comparison
The Australian Signals Directorate (ASD) rates authentication methods based on their resilience to attacks like phishing and account takeover. While their framework is widely respected, some ratings — such as SMS OTP’s ‘Medium’ account takeover resistance — may be optimistic given recent breaches. Industry leaders like CISA and Microsoft per their “Implementing Phishing-Resistant MFA”7 and “Require phishing-resistant multifactor authentication for administrators”8, advocate for phishing-resistant MFA (e.g., FIDO2 security keys) as the highest standard, aligning with ASD’s top-tier rankings.
Implementation Considerations
When selecting and implementing MFA solutions, organizations should consider:
1. Security Requirements and Threat Model
Different sectors face varying threat levels. Financial institutions, government agencies, and healthcare organizations typically require the strongest authentication mechanisms due to the sensitive nature of their data and regulatory requirements.
2. User Experience and Adoption
Security measures that create significant friction often lead to workarounds that ultimately undermine security. The ACSC recommends balancing security requirements with usability to ensure high adoption rates.
3. Cost and Resource Implications
Implementation costs vary significantly across MFA methods:
- SMS authentication: Low initial cost but ongoing operational expenses
- Authenticator apps: Low to medium implementation cost
- Hardware tokens/security keys: Medium to high cost depending on scale
- Biometric systems: Often high initial investment with integration requirements
4. Recovery and Fallback Mechanisms
All authentication systems require robust recovery processes for scenarios such as lost devices or unavailable biometrics. Paradoxically, these necessary recovery mechanisms can sometimes introduce vulnerabilities if not carefully designed.
Future Trends in Multi-Factor Authentication
Several trends are shaping the evolution of MFA:
- Passwordless Authentication: Moving beyond passwords entirely, using combinations of other factors for more secure and convenient authentication.
- Zero Trust Architecture Integration: MFA becoming a cornerstone of zero trust security models that verify every access request regardless of source.
- Adaptive Authentication: Systems that dynamically adjust security requirements based on risk assessment and user behavior patterns.
- Decentralized Identity and Blockchain: Emerging approaches that give users greater control over their digital identities while maintaining strong security.
- Continuous Authentication: Shifting from point-in-time verification to ongoing assessment throughout user sessions.
Recommendation Framework
When selecting MFA methods, organizations should apply this evaluation framework:
- Assess the specific threat landscape for your organization and industry
- Identify the security-usability balance appropriate for different user groups
- Consider the technical environment and integration requirements
- Evaluate total cost of ownership, including implementation, training, support, and maintenance
- Plan for staged implementation, prioritizing high-value systems and accounts
Conclusion
Multi-factor authentication represents one of the most effective security controls available to organizations today. While no single approach works optimally for all situations, the significant security improvements offered by any properly implemented MFA solution make it an essential component of modern cybersecurity strategy.
As attack methods continue to evolve, organizations should regularly reassess their authentication mechanisms to ensure they maintain an appropriate security posture. The Australian Cyber Security Centre recommends that all organizations implement MFA as part of the “Essential Eight“9 mitigation strategies, regardless of size or sector.
By understanding the comparative strengths and limitations of different MFA methods, organizations can make informed decisions that balance security requirements, usability considerations, and implementation constraints to protect their digital assets effectively.
References
- Microsoft, “One simple action you can take to prevent 99.9 percent of attacks on your accounts”, 2019 https://www.microsoft.com/en-us/security/blog/2019/08/20/one-simple-action-you-can-take-to-prevent-99-9-percent-of-account-attacks/ ↩︎
- Australian Cyber Security Centre (ACSC), “Implementing multi-factor authentication”, 2023 https://www.cyber.gov.au/resources-business-and-government/maintaining-devices-and-systems/system-hardening-and-administration/system-hardening/implementing-multi-factor-authentication
↩︎ - Google “New research: How effective is basic account hygiene at preventing hijacking”, 2019 https://security.googleblog.com/2019/05/new-research-how-effective-is-basic.html ↩︎
- Google, “Security keys and zero trust”, 2021 https://cloud.google.com/blog/topics/developers-practitioners/security-keys-and-zero-trust ↩︎
- Institute of Electrical and Electronics Engineers (IEEE), “Lightweight three-factor authentication and key agreement protocol for internet-integrated wireless sensor networks”, 2017 https://ieeeaccess.ieee.org/tag/smart-cards/ ↩︎
- Microsoft, “How effective is multifactor authentication at deterring cyberattacks?”, https://cdn-dynmedia-1.microsoft.com/is/content/microsoftcorp/microsoft/final/en-us/microsoft-brand/documents/mfa-microsoft-research-paper-update-347347.pdf?culture=en-us&country=us
↩︎ - Cybersecurity and Infrastructure Security Agency (CISA), “Implementing Phishing-Resistant MFA”, 2022 https://www.cisa.gov/sites/default/files/publications/fact-sheet-implementing-phishing-resistant-mfa-508c.pdf
↩︎ - Microsoft, “Require phishing-resistant multifactor authentication for administrators”, 2024 https://learn.microsoft.com/en-us/entra/identity/conditional-access/policy-admin-phish-resistant-mfa ↩︎
- Australian Cyber Security Centre (ACSC), “Essential Eight” https://www.cyber.gov.au/resources-business-and-government/essential-cybersecurity/essential-eight
↩︎
At Christian Sajere Cybersecurity and IT Infrastructure, we understand the vital importance of robust identity verification in today’s digital landscape. Our comprehensive analysis of multi-factor authentication methods empowers your organization to implement the optimal security solution for your specific needs. Let us guide you toward enhanced protection.
Related Blog Posts
- Securing Microsoft 365 Email Environments: A Comprehensive Guide
- Crisis Communication During Security Incidents: A Strategic Approach
- Building a Security Operations Center (SOC): Key Components
- Implementing Single Sign-On: Pros, Cons, and Best Practices
- Backup and Recovery: Building Resilience Against Ransomware
- Continuous Compliance Monitoring Through Automation
- Comprehensive Security for Remote Workforces: Safeguarding the Distributed Enterprise