The proliferation of Internet of Things (IoT) devices in enterprise environments has revolutionized operational efficiency, workplace automation, and data-driven decision making. However, this rapid adoption has introduced significant security challenges that organizations must address to protect their networks, data, and infrastructure. Verizon in “5G and IoT: Making connections to change the world”1 estimates 27 billion IoT devices by 2025, with enterprise environments accounting for a significant percentage of it.
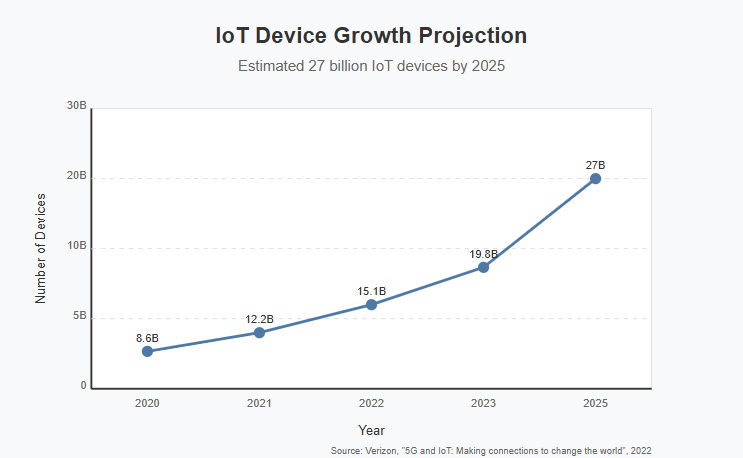
This article examines the most pressing IoT security challenges facing enterprise environments today, providing practical solutions and guidance for organizations looking to secure their IoT infrastructure without sacrificing the benefits these technologies provide.
The Expanding IoT Attack Surface
The enterprise IoT ecosystem has expanded beyond traditional IT infrastructure to include operational technology (OT), industrial control systems, smart building technology, and various employee productivity devices. This convergence has created a substantially larger attack surface that cybercriminals are actively targeting.
ASD’s Cyberthreat Report 2022-20232 acknowledges increasing threats from systems connected to enterprise or critical infrastructure networks. The primary challenge stems from the sheer volume and diversity of devices connecting to enterprise networks, each potentially introducing unique vulnerabilities.
Authentication and Access Control Weaknesses
One of the most significant security challenges in enterprise IoT deployments is inadequate authentication mechanisms. Many IoT devices ship with default credentials, weak password policies, or limited support for modern authentication protocols.
According to IBM Security’s 2024 X-Force Threat Intelligence Index3, weak authentication is a significant security risk. The report emphasizes that attackers increasingly exploit valid accounts rather than hacking into networks, making identity-based attacks a preferred method. The challenge is compounded by the operational constraints of many IoT devices, which may have limited processing capabilities, making robust authentication difficult to implement.
Common Authentication Issues in Enterprise IoT
- Default credentials left unchanged (found in 39% of enterprise IoT deployments)
- Lack of multi-factor authentication support
- Absence of certificate-based authentication
- Hardcoded credentials in firmware or applications
- Limited or no support for authentication protocol updates
Microsoft emphasizes the benefits of zero-trust security models in reducing cyber risks. Its “Zero Trust Adoption Report: How does your organization compare?4” highlights that 76% of organizations are in the process of implementing zero-trust strategies. Organizations implementing zero-trust architectures specifically designed for IoT environments significantly reduce their risk of successful attacks. This approach treats every device, user, and connection as potentially compromised, requiring continuous verification regardless of location.
Lack of Visibility and Management Tools
Enterprise security teams face significant challenges gaining visibility into IoT device activity and behavior. Unlike traditional IT assets, many IoT devices lack comprehensive logging capabilities, making it difficult to monitor for suspicious behavior or unauthorized access attempts.
Verizon’s IoT Security Insights5 states that 62% of companies now have mature IoT deployments, but many still lack full visibility into device interactions. It recommends advanced analytics and AI-driven monitoring to address this issue. This blind spot creates opportunities for attackers to maintain persistent access while evading detection.
Google’s State of Cloud Threat Detection and Response Report6 and Threat Horizons Report7discuss the benefits of comprehensive IoT asset management in improving security operations. Implementing these visibility solutions often requires specialized tools that can identify and monitor IoT-specific protocols and behaviors.
Patching and Update Challenges
Maintaining current security patches across an enterprise IoT ecosystem presents unique operational challenges. Many IoT devices:
- Lack automated update mechanisms
- Require physical access or specialized tools for updates
- Have firmware updates that risk operational disruption
- May no longer be supported by manufacturers
- Operate in critical environments where downtime is costly
Data Privacy and Compliance Issues
Enterprise IoT deployments collect vast amounts of data, much of which may be subject to regulatory requirements or contain sensitive information. Securing this data throughout its lifecycle — from collection and transmission to storage and processing — presents significant challenges. The challenge is particularly acute in multi-jurisdictional operations where different privacy regulations may apply.
Common IoT Data Privacy Challenges
- Unencrypted data transmission between devices and gateways
- Insufficient data minimization practices
- Unclear data retention policies
- Limited user controls over data collection
- Complex consent management across diverse device types
Network Segmentation and Architectural Challenges
Traditional network security architectures often prove inadequate for securing enterprise IoT ecosystems. The diverse nature of IoT devices — from building management systems to employee wearables — requires thoughtful network segmentation and security zone implementation.
The Australian Signals Directorate recommends implementing micro-segmentation for IoT environments, noting that organizations following this guidance experience fewer lateral movement attacks. However, implementing effective segmentation requires careful planning to avoid disrupting legitimate device communication.
Organizations’ network architecture redesign could be the biggest challenge when securing enterprise IoT deployments. The complexity increases in environments where operational technology (OT) and IT networks converge, requiring security teams to understand industrial protocols and operational requirements.
Supply Chain Security Considerations
Enterprise IoT security extends beyond an organization’s perimeter to include the entire supply chain of device manufacturers, software providers, and service integrators. Compromises anywhere in this chain can introduce vulnerabilities into enterprise environments.
Google Cloud’s 2025 Cybersecurity Forecast Report8 discusses emerging security threats, including supply chain attacks targeting IoT device firmware and components. These sophisticated attacks are particularly concerning as they can impact devices before they arrive at the enterprise.
Supply Chain Security Best Practices
- Vendor security assessment frameworks specifically for IoT providers
- Component verification and firmware validation processes
- Contractual security requirements for IoT vendors
- Regular security reassessment of deployed devices
- Hardware-based root of trust verification, where possible
Practical Recommendations for Enterprise IoT Security
Based on guidance from leading security organizations and research, enterprises should consider implementing the following measures to address IoT security challenges:
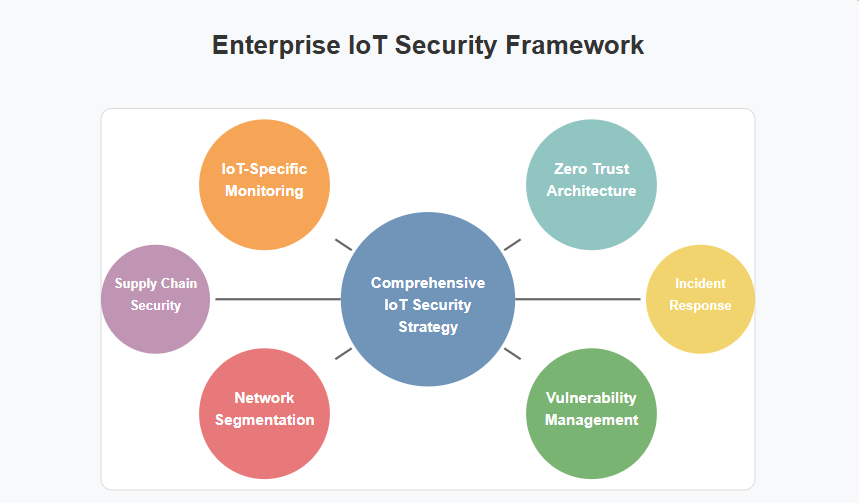
1. Develop a Comprehensive IoT Security Strategy
According to the ACSC’s “IoT Secure by Design guidance for manufacturers“9, organizations should extend their security strategy to explicitly address IoT devices, establishing clear policies for acquisition, deployment, management, and retirement.
2. Implement IoT-Specific Monitoring Solutions
IBM Security recommends deploying specialized monitoring tools that can baseline normal IoT device behavior and detect anomalies that might indicate compromise. These solutions should integrate with existing security information and event management (SIEM) systems.
3. Adopt Zero Trust Architecture for IoT Environments
In “IoT Secure by Design guidance for manufacturers,”10 the Australian Cyber Security Centre (ACSC) advocates implementing a zero trust model specifically adapted for IoT environments, focusing on strict device authentication, least privilege access, and continuous monitoring.
4. Establish IoT Network Segmentation
Creating dedicated network segments for IoT devices with appropriate access controls and monitoring can significantly reduce risk. It is recommended to implement both logical and physical segmentation where critical systems are involved.
5. Develop an IoT Vulnerability Management Program
Enterprises should establish systematic processes for identifying, assessing, and remediating vulnerabilities across their IoT ecosystem. This includes regular scanning, prioritized patching, and compensating controls where updates aren’t feasible.
6. Address Supply Chain Security
It is recommended to implement a formal vendor security assessment process specifically for IoT providers, incorporating hardware security requirements and ongoing security performance metrics.
7. Prepare for IoT Security Incidents
The ACSC emphasizes the importance of including IoT-specific scenarios in incident response planning, ensuring teams have the tools and knowledge to effectively respond to compromises involving these devices.
Conclusion
As enterprises continue to expand their IoT deployments, security challenges will persist and evolve. Organizations that take a proactive, structured approach to IoT security — implementing appropriate technical controls, processes, and policies — can significantly reduce their risk while maximizing the operational benefits these technologies provide.
The rapidly evolving nature of the IoT threat landscape requires security teams to remain vigilant, continually assessing new threats and adapting their defenses accordingly. By leveraging guidance from leading security organizations and implementing the recommendations outlined in this article, enterprises can build resilient IoT ecosystems that support innovation while maintaining an appropriate security posture.
References
- Verizon, “5G and IoT: Making connections to change the world”, 2022 https://www.verizon.com/about/news/5g-iot-together-changing-our-world ↩︎
- Australian Signals Directorate (ASD), “Cyberthreat Report 2022-2023”, 2023 https://www.cyber.gov.au/about-us/view-all-content/reports-and-statistics/asd-cyber-threat-report-july-2022-june-2023 ↩︎
- IBM, “Security’s 2024 X-Force Threat Intelligence Index,” 2024 https://newsroom.ibm.com/2024-02-21-IBM-Report-Identity-Comes-Under-Attack,-Straining-Enterprises-Recovery-Time-from-Breaches ↩︎
- Microsoft, “Zero Trust Adoption Report: How does your organization compare?”, 2021 https://www.microsoft.com/en-us/security/blog/2021/07/28/zero-trust-adoption-report-how-does-your-organization-compare/ ↩︎
- Verizon, “IoT Security Insights”, 2025 https://www.verizon.com/business/resources/articles/s/understanding-iot-solutions-for-a-secure-connected-future/ ↩︎
- Google, “State of Cloud Threat Detection and Response Report,” 2025 https://services.google.com/fh/files/misc/gcat_cloud_dr_survey_report_2023.pdf ↩︎
- Google, “Threat Horizons Report” 2025 https://services.google.com/fh/files/misc/threat_horizons_report_h1_2025.pdf ↩︎
- Google Cloud, “2025 Cybersecurity Forecast Report”, 2025 https://cloud.google.com/blog/products/identity-security/cloud-ciso-perspectives-our-2025-cybersecurity-forecast-report ↩︎
- Australian Cyber Security Centre (ACSC), “IoT Secure by Design guidance for manufacturers“, 2023 https://www.cyber.gov.au/resources-business-and-government/maintaining-devices-and-systems/system-hardening-and-administration/system-hardening/iot-secure-design-guidance-manufacturers ↩︎
- Australian Cyber Security Centre (ACSC), “IoT Secure by Design guidance for manufacturers“, 2023 https://www.cyber.gov.au/resources-business-and-government/maintaining-devices-and-systems/system-hardening-and-administration/system-hardening/iot-secure-design-guidance-manufacturers ↩︎
Facing escalating IoT security threats across your enterprise? Our comprehensive vulnerability management system identifies and mitigates risks before they become breaches. Let us fortify your connected ecosystem today
Related Blog Posts
- Zero Trust for Remote Work: Practical Implementation
- DevSecOps for Cloud: Integrating Security into CI/CD
- Customer Identity and Access Management (CIAM): The Competitive Edge for Australian Businesses
- Infrastructure as Code Security Testing: Securing the Foundation of Modern IT
- Measuring DevSecOps Success: Metrics and KPIs
- Secure CI/CD Pipelines: Design and Implementation
- Certificate-Based Authentication for Users and Devices: A Comprehensive Security Strategy


