In today’s rapidly evolving cybersecurity landscape, organizations face an unprecedented surge in sophisticated cyber threats that demand not just reactive responses, but proactive preparation for potential investigations. Forensic readiness represents a strategic approach to cybersecurity that enables organizations to collect, preserve, and analyze digital evidence effectively when security incidents occur. As cybercriminals increasingly leverage advanced techniques and AI-powered attacks, the need for comprehensive forensic preparation has never been more critical.
The Current Threat Landscape
Recent data reveals alarming trends in cybersecurity threats that underscore the importance of forensic readiness. According to the Verizon 2025 Data Breach Investigations Report,1 which analyzed 22,052 real-world security incidents, of which 12,195 were confirmed data breaches across 139 countries, organizations are indeed facing a growing wave of evolving attack vectors. The report indicates that attacks exploiting vulnerabilities as the critical path to initiate a breach rose to 20% of breaches, representing a 34% increase compared to the previous year.
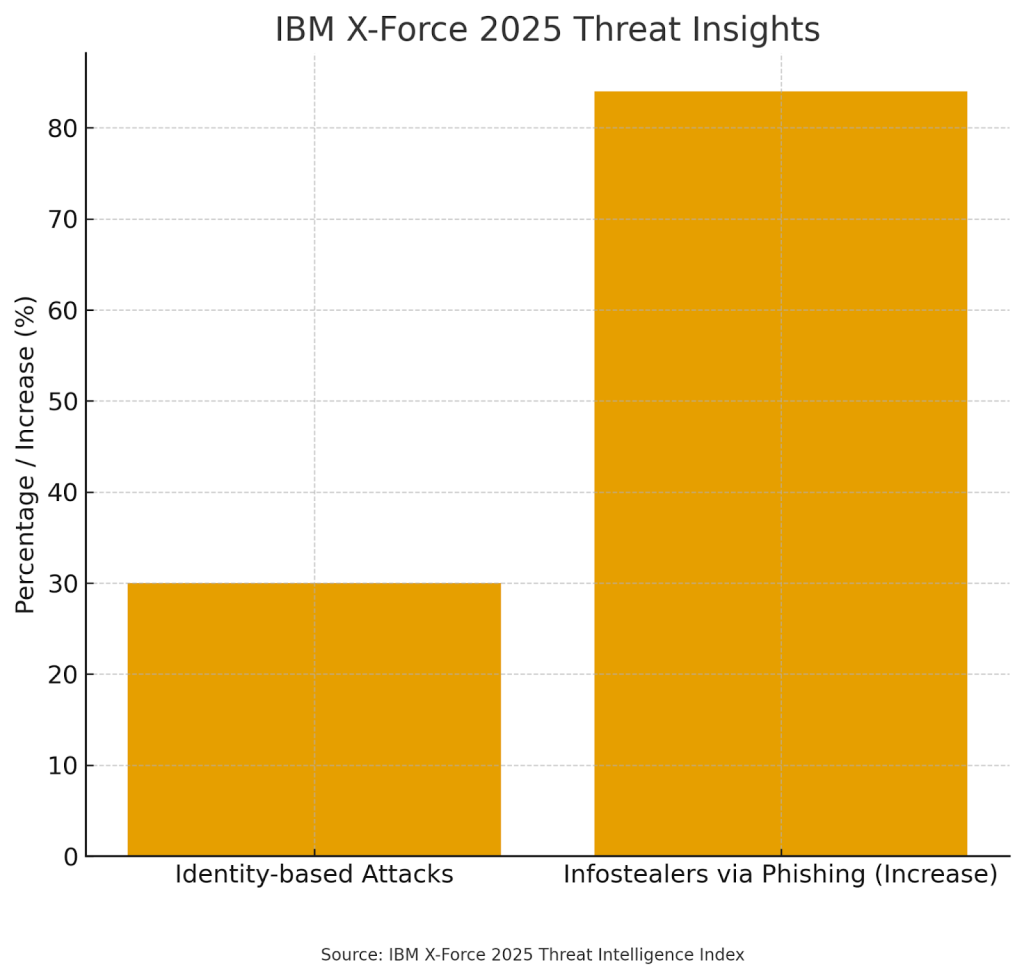
The IBM X-Force 2025 Threat Intelligence Index2 provides additional concerning insights, revealing that identity-based attacks make up 30% of total intrusions and infostealers delivered via phishing emails per week increases by 84%. These statistics highlight the sophisticated nature of modern attacks and the critical need for organizations to be prepared to investigate and respond to security incidents effectively.
Furthermore, the evolution of ransomware tactics has created new challenges for forensic investigations. Roughly one-third of all breaches involved Ransomware or some other Extortion technique, with attackers now employing multiple extortion methods to maximize their impact and financial gains.
Understanding Forensic Readiness
Forensic readiness encompasses the proactive measures organizations implement to ensure they can conduct effective digital forensic investigations when security incidents occur. This approach goes beyond traditional incident response by establishing the necessary infrastructure, processes, and capabilities to preserve and analyze digital evidence systematically.
The National Institute of Standards and Technology (NIST), through its Information Technology Laboratory (ITL) Cybersecurity and Privacy Program, reported significant progress during fiscal year 2024 in addressing emerging challenges and opportunities in security and privacy. According to its Fiscal Year 2024 Cybersecurity and Privacy Annual Report,3 the program advanced research and practical applications across priority areas such as post-quantum cryptography, identity and access management, privacy, risk management, trustworthy networks and platforms, and projects led by the National Cybersecurity Center of Excellence (NCCoE). While digital forensics was not listed as one of the explicit priority areas in the 2024 report, NIST has long recognized the importance of forensic capabilities, particularly through earlier publications like SP 800-86 and SP 800-101, which guide the integration of forensic techniques into incident response. Taken together, these efforts underscore the critical role that forensic practices play in comprehensive cybersecurity strategies.
Key Components of Forensic Readiness
1. Evidence Collection Infrastructure
Organizations must establish robust systems for automatically collecting and preserving digital evidence across their entire IT infrastructure. This includes implementing comprehensive logging mechanisms, maintaining accurate system inventories, and ensuring proper time synchronization across all systems. The evidence collection infrastructure should be designed to capture data from multiple sources, including network traffic, system logs, user activities, and application interactions.
The complexity of modern IT environments, particularly with the increasing adoption of cloud services and hybrid infrastructures, requires sophisticated evidence collection capabilities. Organizations must ensure they can collect evidence from traditional on-premises systems, cloud environments, and mobile devices while maintaining the integrity and authenticity of the data.
2. Data Preservation and Chain of Custody
Maintaining the integrity of digital evidence requires robust data preservation mechanisms and strict chain of custody procedures. Organizations must implement automated backup systems that create forensically sound copies of critical data, ensuring that evidence remains unaltered from the time of collection through the completion of any investigation.
The chain of custody documentation must track every access to and handling of digital evidence, creating an unbreakable record that can withstand legal scrutiny. This includes implementing access controls, audit trails, and verification mechanisms that ensure only authorized personnel can access evidence and that all interactions are properly documented.
3. Incident Detection and Response Integration
Forensic readiness must be tightly integrated with incident detection and response capabilities. Organizations should implement advanced monitoring systems that can automatically identify potential security incidents and trigger evidence preservation processes. This integration ensures that critical evidence is collected and preserved from the earliest stages of an incident, maximizing the potential for successful investigation and remediation.
The integration should also include automated alerting mechanisms that notify forensic teams immediately when potential incidents are detected, enabling rapid response and evidence collection before critical data is lost or compromised.
4. Legal and Regulatory Compliance
Organizations must ensure their forensic readiness programs comply with relevant legal and regulatory requirements. This includes understanding data protection laws, evidence handling requirements, and disclosure obligations that may apply to their specific industry or jurisdiction.
Compliance considerations must also address international data transfer restrictions, particularly for organizations operating across multiple countries or using cloud services provided by vendors in different jurisdictions. The forensic readiness program must be designed to navigate these complex legal requirements while maintaining the effectiveness of investigation capabilities.
Current Challenges in Forensic Readiness
The Human Element
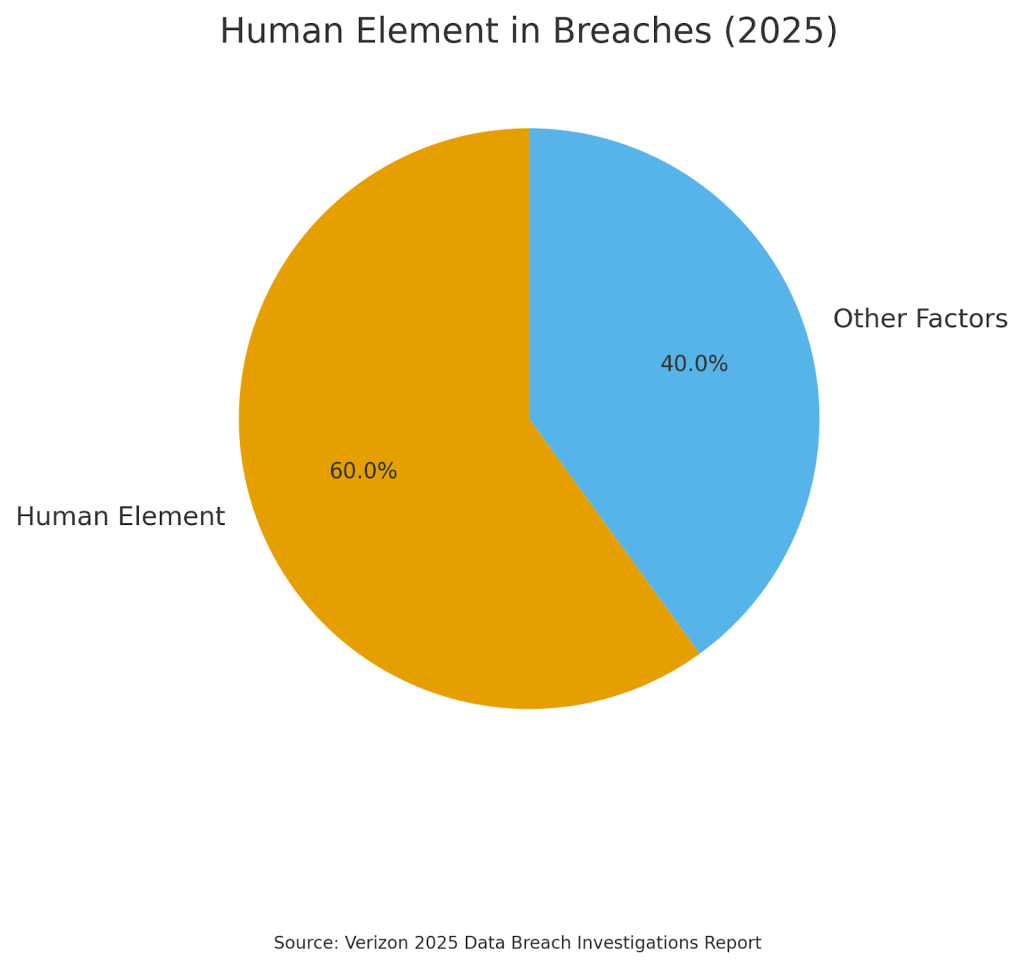
Despite technological advances, human factors continue to play a significant role in cybersecurity incidents. The human element was a component of 60% of breaches, according to Verizon’s 2025 Data Breach Investigations Report.4 This statistic highlights the importance of considering human behavior and potential insider threats in forensic readiness planning.
Organizations must prepare to investigate incidents involving both malicious insider activities and unintentional human errors. This requires implementing monitoring systems that can detect anomalous user behavior while respecting privacy rights and maintaining employee trust.
Supply Chain Complexities
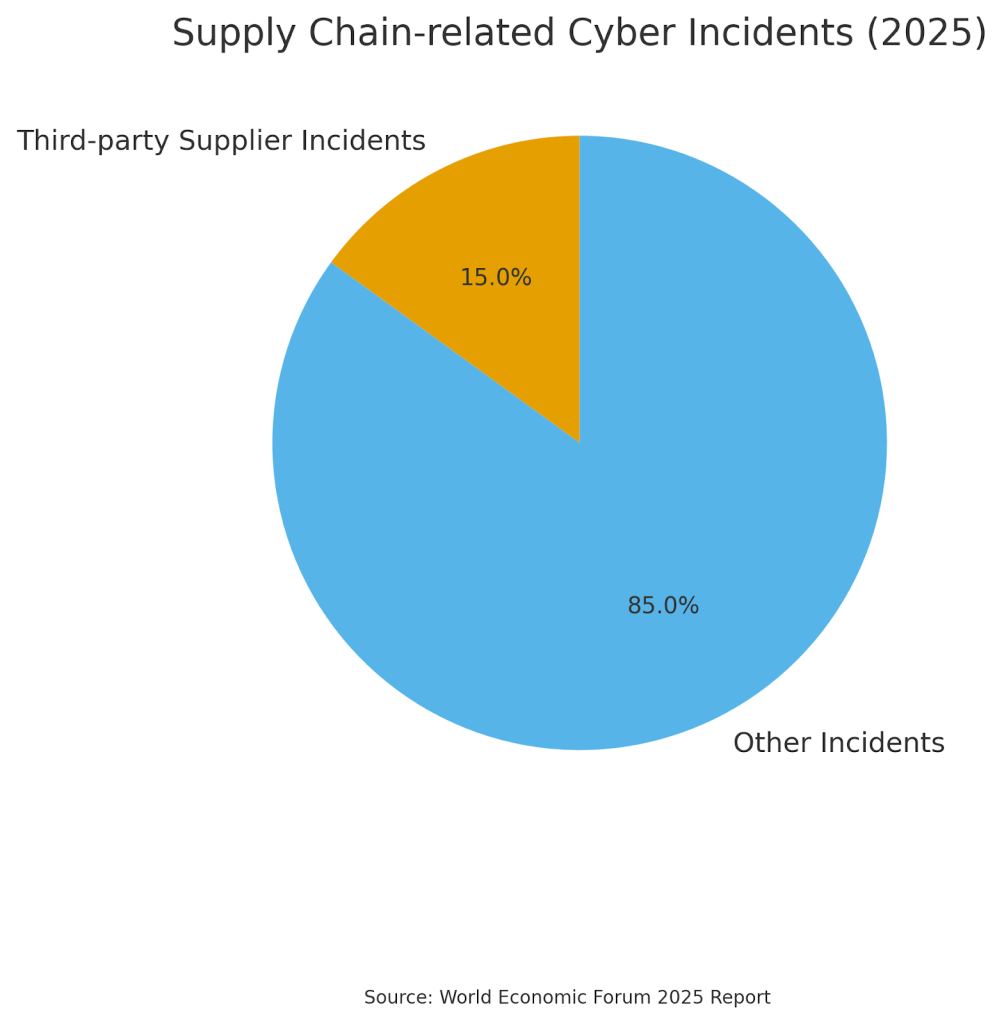
The increasing interconnectedness of modern business environments has created new challenges for forensic readiness. Data from the World Economic Forum’s Three key ways to make supply chains more resilient to cyber risks5 shows that 15% of cyber incidents involved a third-party supplier. Organizations must prepare to investigate incidents that may originate from third-party suppliers, cloud service providers, or other business partners.
This complexity requires extending forensic readiness capabilities beyond organizational boundaries, establishing agreements with suppliers and partners that ensure access to relevant evidence when incidents occur. Organizations must also develop capabilities to investigate incidents involving multiple parties and coordinate evidence collection across different entities.
Evolving Attack Techniques
The sophistication of modern cyber attacks continues to evolve, with threat actors increasingly leveraging artificial intelligence and advanced techniques to evade detection. Threat actors add AI to their toolboxes, using these technologies to create more convincing phishing emails, develop sophisticated malware, and scale their attacks.
This evolution requires organizations to continuously update their forensic readiness capabilities, implementing new technologies and techniques to investigate AI-powered attacks and other advanced threats. Forensic teams must stay current with emerging attack methods and develop the skills and tools necessary to analyze evidence from increasingly sophisticated incidents.
Technology and Tools for Forensic Readiness
Advanced Analytics and Machine Learning
Modern forensic investigations increasingly rely on advanced analytics and machine learning technologies to process large volumes of digital evidence efficiently. These tools can identify patterns, anomalies, and relationships in data that would be impossible to detect through manual analysis.
Organizations should implement analytics platforms that can process data from multiple sources, correlate events across different systems, and provide investigators with actionable insights. Machine learning algorithms can help identify indicators of compromise, trace attack paths, and predict potential future incidents based on historical patterns.
Cloud-Based Forensic Platforms
The migration to cloud environments requires organizations to adapt their forensic readiness capabilities to handle cloud-based evidence. This includes implementing tools that can collect evidence from cloud services, maintain proper chain of custody for cloud-stored data, and ensure compliance with cloud provider terms of service and legal requirements.
Cloud-based forensic platforms offer scalability and flexibility advantages, allowing organizations to rapidly deploy investigation capabilities and process large volumes of data without investing in extensive on-premises infrastructure.
Automation and Orchestration
Given the scale and complexity of modern security incidents, organizations must leverage automation and orchestration technologies to streamline forensic processes. Automated evidence collection, analysis, and reporting can significantly reduce investigation timelines and improve the accuracy of forensic findings.
Orchestration platforms can coordinate multiple forensic tools, manage workflow processes, and ensure consistent application of investigation procedures across different incident types and organizational units.
Global Perspectives on Forensic Readiness
Australian Cybersecurity Landscape
For Australian organizations, forensic readiness is particularly important given the country’s position in the Asia-Pacific region.According to IBM’s X-Force 2025 Threat Intelligence Index,6 Asia-Pacific region sees a 13% increase in attacks, making it the most targeted region globally, accounting for 34% of all incidents investigated in recent studies.
Australian organizations must prepare for the specific threats targeting the region, including attacks on critical infrastructure, manufacturing facilities, and financial institutions. The Australian Signals Directorate and Australian Cyber Security Centre provide valuable guidance and resources, such as the Guidance on digital forensics and protective monitoring specifications for producers of network devices and appliances7 for organizations developing forensic readiness capabilities.
Regulatory Environment
The Australian regulatory environment continues to evolve, with new requirements for incident reporting and evidence preservation. Organizations must ensure their forensic readiness programs comply with Australian privacy laws, industry-specific regulations, and emerging cybersecurity directives.
The integration of forensic readiness with broader compliance programs can provide organizations with significant advantages, ensuring they can meet regulatory requirements while maintaining effective investigation capabilities.
Implementation Strategies
Phased Approach
Organizations should implement forensic readiness capabilities using a phased approach that prioritizes critical assets and high-risk areas. The initial phase should focus on establishing basic evidence collection and preservation capabilities for the most critical systems and data.
Subsequent phases can expand coverage to include additional systems, implement advanced analytics capabilities, and integrate with external partners and suppliers. This approach allows organizations to demonstrate value from their forensic readiness investments while building comprehensive capabilities over time.
Training and Skills Development
Successful forensic readiness requires skilled personnel who can operate investigation tools, analyze evidence, and coordinate with legal and regulatory authorities. Organizations must invest in training programs that develop both technical and procedural skills among their forensic teams.
Cross-training initiatives can help ensure that forensic capabilities are distributed across the organization, reducing dependence on individual specialists and improving overall resilience. Regular training exercises and simulations can help teams maintain their skills and identify areas for improvement.
Testing and Validation
Regular testing and validation of forensic readiness capabilities is essential to ensure they remain effective as technology and threats evolve. Organizations should conduct regular forensic exercises that simulate various incident scenarios and test their ability to collect, preserve, and analyze evidence effectively.
These exercises should include coordination with external stakeholders, including law enforcement agencies, legal counsel, and regulatory authorities. Testing results should be used to identify gaps and improvement opportunities in forensic readiness programs.
Future Trends and Considerations
Artificial Intelligence Integration
The integration of artificial intelligence into forensic investigations will continue to evolve, offering new capabilities for evidence analysis and case management. However, this integration also raises new challenges related to the admissibility of AI-generated findings and the need for human oversight in automated processes.
Organizations must carefully consider how to leverage AI technologies while maintaining the reliability and legal defensibility of their forensic findings. This includes implementing proper validation procedures, maintaining human oversight, and ensuring transparency in AI-driven analysis processes.
Quantum Computing Implications
The eventual emergence of practical quantum computing capabilities will have significant implications for digital forensics, particularly in areas such as encryption and data security. Organizations should begin considering how quantum technologies might affect their forensic capabilities and evidence preservation requirements.
While practical quantum computing remains years away, early preparation can help organizations adapt their forensic readiness programs to address these future challenges.
Return on Investment and Business Value
Cost-Benefit Analysis
Implementing comprehensive forensic readiness capabilities requires significant investment in technology, personnel, and processes. However, the potential benefits extend far beyond incident response, including improved compliance posture, reduced investigation timelines, and enhanced ability to recover from security incidents.
Organizations should conduct thorough cost-benefit analyses that consider both direct costs and indirect benefits of forensic readiness investments. These analyses should include factors such as regulatory compliance costs, potential legal liabilities, and business disruption risks associated with inadequate forensic capabilities.
Integration with Business Processes
Forensic readiness should be integrated with broader business processes and risk management frameworks to maximize value and ensure sustainability. This integration can help organizations identify synergies with other security investments and demonstrate clear business value from forensic readiness initiatives.
Regular reporting on forensic readiness metrics and outcomes can help maintain executive support and ensure continued investment in these critical capabilities.
Conclusion
Forensic readiness represents a critical component of modern cybersecurity strategy, enabling organizations to respond effectively to security incidents while meeting legal and regulatory requirements. As cyber threats continue to evolve and increase in sophistication, the importance of proactive forensic preparation will only grow.
Organizations that invest in comprehensive forensic readiness programs will be better positioned to investigate incidents quickly, minimize business disruption, and recover from security breaches effectively. The key to success lies in implementing a holistic approach that combines technology, processes, and people to create robust investigation capabilities.
The current threat landscape, characterized by sophisticated attack techniques, supply chain complexities, and regulatory requirements, demands that organizations move beyond reactive incident response to proactive forensic readiness. By establishing comprehensive evidence collection and preservation capabilities, organizations can ensure they are prepared to investigate and respond to whatever challenges the future may bring.
Sources and References
- Verizon. (2025). 2025 Data Breach Investigations Report. https://www.verizon.com/business/resources/Tbb1/reports/2025-dbir-data-breach-investigations-report.pdf ↩︎
- IBM. (2025). X-Force 2025 Threat Intelligence Index. https://www.ibm.com/thought-leadership/institute-business-value/en-us/report/2025-threat-intelligence-index ↩︎
- National Institute of Standards and Technology (NIST). (2025). Fiscal Year 2024 Cybersecurity and Privacy Annual Report. https://csrc.nist.gov/pubs/sp/800/236/final ↩︎
- Verizon. (2025). 2025 Data Breach Investigations Report. https://www.verizon.com/business/resources/Tbb1/reports/2025-dbir-data-breach-investigations-report.pdf ↩︎
- World Economic Forum. (2025). Three key ways to make supply chains more resilient to cyber risks. https://www.weforum.org/stories/2025/04/three-key-directions-for-the-cyber-resiliency-crisis-in-global-supply-chains/ ↩︎
- IBM. (2025). X-Force 2025 Threat Intelligence Index. https://www.ibm.com/thought-leadership/institute-business-value/en-us/report/2025-threat-intelligence-index ↩︎
- Australian Cyber Security Centre. (2025). Guidance on digital forensics and protective monitoring specifications for producers of network devices and appliances. Australian Signals Directorate. https://www.cyber.gov.au/resources-business-and-government/maintaining-devices-and-systems/system-hardening-and-administration/network-hardening/securing-edge-devices/guidance-on-digital-forensics-and-protective-monitoring-specifications-for-producers-of-network-devices-and-appl ↩︎
Related Blog Posts
- Privacy by Design: Implementation Framework for Modern Organizations
- Security Awareness Program Design: Beyond Compliance
- Vulnerability Management for Third-Party Applications: A Critical Security Imperative
- Securing API Gateways in Cloud-Native Architectures
- Data Subject Access Requests: Handling Process – A Comprehensive Guide for Australian Organizations
- Gamification in Security Awareness Training: Revolutionizing Cybersecurity Education Through Strategic Engagement
- Anonymization vs. Pseudonymization Techniques: A Comprehensive Guide for Modern Data Protection


