In today’s rapidly evolving digital landscape, where cyber threats are becoming increasingly sophisticated and data breaches carry unprecedented costs, secure code development has emerged as a critical cornerstone of organizational cybersecurity strategy. The global average cost of a data breach reached new heights in 2024, marking a 10% increase over the previous year according to IBM’s Cost of a Data Breach Report1. This alarming trend underscores the urgent need for robust security measures throughout the software development lifecycle, with secure code review standing as one of the most effective preventive controls available to organizations.
Code review for security represents a systematic examination of source code designed to identify vulnerabilities, security flaws, and potential attack vectors before they can be exploited in production environments. This process serves as a critical checkpoint in the development pipeline, enabling teams to catch security issues early when they are significantly less expensive and disruptive to remediate. Fixing a security vulnerability in production can cost up to 30 times more than addressing it during the development phase, highlighting the substantial return on investment that effective code review practices can deliver, according to NIST’s The Economic Impacts of Inadequate Infrastructure for Software Testing.2
The Current Threat Landscape and Code Security Challenges
The cybersecurity threat landscape has undergone dramatic transformation in recent years, with state-sponsored attacks, ransomware campaigns, and sophisticated malware becoming increasingly prevalent. Microsoft’s Digital Defense Report 20243 reveals that nation-state threat actors are conducting operations for financial gain and enlisting cybercriminals to collect intelligence, with education and research sectors becoming the second-most targeted by these advanced persistent threats.
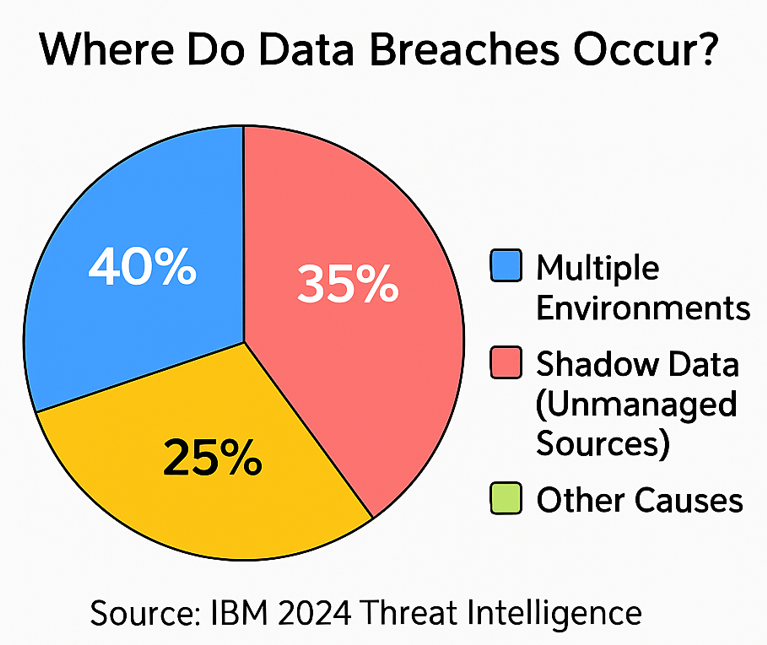
Contemporary applications face unique security challenges that traditional security measures often fail to address adequately. Modern software architectures frequently involve complex ecosystems of microservices, third-party libraries, cloud deployments, and API integrations, each introducing potential attack surfaces. IBM’s 2024 threat intelligence data as seen in “Third-party access: The overlooked risk to your data protection plan,”4 shows that 40% of breaches involved data stored across multiple environments, while more than one-third involved shadow data stored in unmanaged sources, illustrating the complexity of securing modern distributed systems.
The integration of artificial intelligence and machine learning technologies into business operations has created new attack vectors and security considerations. With 42% of companies now integrating AI into at least one business function according to IBM’s research in “Data Suggests Growth in Enterprise Adoption of AI is Due to Widespread Deployment by Early Adopters, But Barriers Keep 40% in the Exploration and Experimentation Phases”5, representing a significant increase from the previous year, developers must consider AI-specific vulnerabilities such as model poisoning, adversarial inputs, and data privacy concerns when reviewing code.
Fundamental Principles of Security-Focused Code Review
Effective security code review operates on several core principles that distinguish it from traditional functional code review. The principle of defense in depth requires reviewers to examine code through multiple security lenses, considering not just individual vulnerabilities but also how different components might interact to create security weaknesses. This approach recognizes that no single security control is sufficient, and multiple layers of protection must be implemented throughout the codebase.
The principle of least privilege mandates that code should operate with the minimum necessary permissions and access rights. During security review, developers must scrutinize authentication and authorization mechanisms, ensuring that users and processes can only access resources essential to their legitimate functions. This principle extends to database connections, file system access, network communications, and API integrations.
Input validation and output encoding represent another fundamental pillar of secure code review. Every point where external data enters the system represents a potential attack vector, whether through user interfaces, API endpoints, file uploads, or database queries. Reviewers must verify that all inputs are properly validated, sanitized, and contextually encoded before use, preventing injection attacks and cross-site scripting vulnerabilities.
Error handling and information disclosure require careful attention during security review. Applications should fail securely, providing minimal information to potential attackers while maintaining appropriate logging for security monitoring. Code reviewers must ensure that error messages, stack traces, and debug information do not reveal sensitive details about system architecture, database schemas, or internal operations.
Essential Security Review Techniques
Static analysis represents one of the most systematic approaches to security code review, involving the examination of source code without executing the program. This technique enables reviewers to identify potential security vulnerabilities, coding standard violations, and logic flaws through automated scanning tools and manual inspection. Static analysis tools can detect common vulnerability patterns such as SQL injection, cross-site scripting, buffer overflows, and cryptographic weaknesses with high accuracy and minimal false positives when properly configured.
Dynamic analysis complements static techniques by examining application behavior during runtime execution. This approach involves testing the application with various inputs, monitoring system calls, network traffic, and memory usage to identify security vulnerabilities that may not be apparent in static code review. Dynamic analysis is particularly effective for detecting race conditions, memory leaks, authentication bypasses, and complex logic vulnerabilities that emerge only during specific execution paths.
Threat modeling integration enhances code review effectiveness by providing structured analysis of potential attack vectors and security requirements. This technique involves systematically identifying assets, threats, vulnerabilities, and countermeasures relevant to the specific application context. Microsoft’s STRIDE methodology6 (Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, Elevation of Privilege) provides a comprehensive framework for analyzing security threats during code review.
Peer review processes establish collaborative security validation through structured examination by multiple team members with complementary expertise. Effective peer review combines security specialists with domain experts and experienced developers to ensure comprehensive coverage of both security and functional requirements. Google’s research demonstrates that code review practices significantly improve software quality and reduce post-release defects when implemented with proper guidelines and tool support.
Critical Vulnerability Categories and Detection Methods
Injection vulnerabilities continue to represent one of the most prevalent and dangerous categories of security flaws in modern applications. SQL injection, command injection, LDAP injection, and other injection attacks occur when untrusted data is sent to interpreters as part of commands or queries. During code review, developers must examine all database interactions, system calls, and external service communications to ensure proper parameterization and input validation.
Cross-site scripting (XSS) vulnerabilities enable attackers to inject malicious scripts into web applications viewed by other users. Code reviewers must scrutinize all points where user-generated content is displayed, ensuring proper output encoding and content security policy implementation. Both reflected and stored XSS vulnerabilities require different detection approaches and remediation strategies.
Authentication and session management flaws represent critical security risks that require careful examination during code review. Reviewers must verify proper password storage using appropriate hashing algorithms, secure session token generation and management, multi-factor authentication implementation, and account lockout mechanisms. These vulnerabilities often result from subtle implementation errors that automated tools may not detect.
Cryptographic vulnerabilities arise from improper implementation of encryption, hashing, digital signatures, and random number generation. Code reviewers must verify the use of approved cryptographic algorithms, proper key management practices, secure random number generation, and appropriate cryptographic protocols. IBM’s security research emphasizes that cryptographic failures often result from implementation details rather than algorithmic weaknesses.
Advanced Security Review Tools and Technologies
Modern security code review relies heavily on sophisticated tooling that can analyze large codebases efficiently and accurately. Static Application Security Testing (SAST) tools such as Microsoft Security Code Analysis, IBM AppScan Source, and Google CodeQL provide automated vulnerability detection capabilities integrated into development workflows. These tools can identify security vulnerabilities early in the development process, often before code is committed to version control systems.
Dynamic Application Security Testing (DAST) tools complement static analysis by testing running applications for security vulnerabilities. These tools simulate attacker behaviors, sending malicious inputs and monitoring application responses to identify vulnerabilities such as injection flaws, authentication bypasses, and configuration errors. Integration of DAST tools with continuous integration pipelines enables automated security testing throughout the development lifecycle.
Interactive Application Security Testing (IAST) combines elements of both SAST and DAST approaches by analyzing applications from within during runtime. IAST tools instrument applications to monitor data flow, function calls, and security-relevant operations, providing detailed vulnerability information with low false positive rates. This approach enables precise vulnerability identification with specific code location information.
Container and infrastructure security scanning tools address the growing security challenges associated with containerized applications and cloud deployments. These tools analyze container images, Kubernetes configurations, and cloud infrastructure templates to identify security misconfigurations, vulnerable dependencies, and compliance violations. Given that 82% of breaches in 2024 are expected to involve cloud-based data, as seen in IBM’s “What is data security posture management (DSPM)?”7, which is based on its Cost of a Data Breach Report 20238, to industry statistics, these capabilities have become essential for comprehensive security review.
Implementation Strategies and Best Practices
Establishing effective security code review processes requires systematic integration with existing development workflows and organizational security policies. Organizations should implement security review checkpoints at multiple stages of the development lifecycle, including design review, implementation review, and pre-deployment validation. This multi-stage approach ensures that security considerations are addressed early and continuously throughout the development process.
Training and skill development represent critical success factors for effective security code review implementation. Development teams require specialized knowledge about common vulnerability patterns, secure coding practices, and security testing techniques. Microsoft’s Secure Development Lifecycle (SDL)9 provides comprehensive guidance for building security expertise within development organizations, emphasizing hands-on training and practical application of security principles.
Tool integration and automation enable scalable security review processes that can keep pace with rapid development cycles. Organizations should establish continuous integration pipelines that automatically execute security scanning tools, generate vulnerability reports, and enforce security quality gates. This automation reduces manual effort while ensuring consistent application of security review standards across all development projects.
Metrics and measurement provide essential feedback for improving security review effectiveness over time. Organizations should track metrics such as vulnerability detection rates, false positive percentages, remediation times, and security defect densities to identify improvement opportunities and demonstrate security program value. IBM’s research indicates that organizations with mature security metrics programs achieve significantly better security outcomes and lower breach costs.
Australian Cybersecurity Context and Compliance Considerations
Australia’s cybersecurity landscape has undergone significant transformation with the introduction of comprehensive legislation and regulatory frameworks designed to enhance national cyber resilience. The Cyber Security Act 202410 represents Australia’s first standalone cybersecurity legislation, establishing mandatory security standards for smart devices and creating new governance structures for incident response and threat intelligence sharing.
The Australian Signals Directorate’s Australian Cyber Security Centre (ASD’s ACSC) provides authoritative guidance for organizations seeking to implement robust cybersecurity practices. The ASD’s Essential Eight mitigation strategies11 include application control and patch management requirements that directly impact secure code development practices. Organizations must ensure that their code review processes align with these national security frameworks to maintain compliance and contribute to Australia’s collective cyber resilience.
The 2023-2030 Australian Cyber Security Strategy12 emphasizes the importance of building cyber resilience through proactive security measures, including secure software development practices. This strategy recognizes that cybersecurity is not merely a technical challenge but a fundamental business and national security imperative that requires comprehensive approaches encompassing people, processes, and technology.
Future Directions and Emerging Technologies
The evolution of artificial intelligence and machine learning technologies is creating new opportunities and challenges for security code review. AI-powered code analysis tools are becoming increasingly sophisticated, capable of identifying complex vulnerability patterns and providing intelligent remediation suggestions. However, these same technologies also introduce new security considerations that require specialized review techniques and expertise.
Quantum computing represents an emerging threat to current cryptographic implementations, requiring organizations to begin transitioning to quantum-resistant algorithms and protocols. Security code review processes must evolve to evaluate quantum readiness and ensure long-term cryptographic security as quantum computing capabilities mature.
DevSecOps integration continues to mature, with security becoming more deeply embedded in development workflows and organizational culture. This trend requires security code review processes to become more collaborative, automated, and integrated with development tools and practices. The goal is to make security an inherent part of software development rather than a separate activity that occurs after development completion.
Conclusion and Strategic Recommendations
Effective security code review represents a critical investment in organizational cybersecurity posture that delivers substantial returns through reduced vulnerability exposure, lower remediation costs, and improved regulatory compliance. As cyber threats continue to evolve and data breach costs reach unprecedented levels, organizations cannot afford to neglect secure development practices.
Success requires a holistic approach that combines appropriate tooling, skilled personnel, well-defined processes, and organizational commitment to security excellence. Organizations should begin by establishing baseline security review capabilities and gradually expanding sophistication and coverage based on risk assessment and resource availability.
The integration of security considerations throughout the development lifecycle, from initial design through deployment and maintenance, ensures that security becomes an inherent characteristic of software systems rather than an afterthought. This proactive approach aligns with both industry best practices and emerging regulatory requirements, positioning organizations for long-term success in an increasingly complex threat environment.
Regular evaluation and improvement of security review processes ensures continued effectiveness as threats evolve and organizational needs change. By investing in security code review capabilities today, organizations can build resilient software systems that protect critical assets and maintain stakeholder trust in an uncertain cybersecurity landscape.
References
- IBM, “Cost of a Data Breach Report”, 2024 https://newsroom.ibm.com/2024-07-30-ibm-report-escalating-data-breach-disruption-pushes-costs-to-new-highs ↩︎
- National Institute of Standards and Technology, “The Economic Impacts of Inadequate Infrastructure for Software Testing“, 2002 https://www.nist.gov/system/files/documents/director/planning/report02-3.pdf ↩︎
- Microsoft, “Digital Defense Report 2024”, https://www.microsoft.com/en-us/security/security-insider/intelligence-reports/microsoft-digital-defense-report-2024 ↩︎
- IBM, “Third-party access: The overlooked risk to your data protection plan”, 2024 https://www.ibm.com/think/insights/third-party-access-the-overlooked-risk-to-data-protection ↩︎
- IBM’s, “Data Suggests Growth in Enterprise Adoption of AI is Due to Widespread Deployment by Early Adopters, But Barriers Keep 40% in the Exploration and Experimentation Phases”, https://newsroom.ibm.com/2024-01-10-Data-Suggests-Growth-in-Enterprise-Adoption-of-AI-is-Due-to-Widespread-Deployment-by-Early-Adopters ↩︎
- Microsoft, “STRIDE methodology”, https://learn.microsoft.com/en-us/archive/msdn-magazine/2006/november/uncover-security-design-flaws-using-the-stride-approach ↩︎
- IBM, “What is data security posture management (DSPM)?”, https://www.ibm.com/think/topics/data-security-posture-management ↩︎
- IBM, “Cost of a Data Breach Report 2023”, https://www.ibm.com/reports/data-breach ↩︎
- Microsoft, “Secure Development Lifecycle (SDL)”, https://www.microsoft.com/en-us/securityengineering/sdl ↩︎
- Australian Government, Department of Home Affairs, “ Cyber Security Act 2024”, https://www.homeaffairs.gov.au/cyber-security-subsite/Pages/cyber-security-act.aspx ↩︎
- Australian Signals Directorate (ASD), “Essential Eight mitigation strategies”, https://www.cyber.gov.au/resources-business-and-government/essential-cybersecurity/essential-eight ↩︎
- Australian Government, Department of Home Affairs, “2023-2030 Australian Cyber Security Strategy”, https://www.homeaffairs.gov.au/about-us/our-portfolios/cyber-security/strategy/2023-2030-australian-cyber-security-strategy ↩︎
At Christian Sajere Cybersecurity and IT Infrastructure, we understand that secure code is the foundation of robust cybersecurity. Our expert team specializes in implementing comprehensive code review processes, advanced security testing tools, and developer training programs that transform your development lifecycle. Let us help you build security into every line of code
Related Blog Posts
- Cryptography Basics for IT Security Professionals: A Comprehensive Guide for Modern Cybersecurity
- AI Ethics and Security: Balancing Innovation and Protection
- Legal Considerations for Penetration Testing in Australia
- Managing Security Debt in Software Development: A Strategic Approach to Long-term Security Excellence
- Adversarial Machine Learning: Understanding the Threats
- Selecting the Right Penetration Testing Partner: A Strategic Guide for Australian Organizations
- Digital Signatures: Implementation and Verification


