In Australia’s rapidly evolving cybersecurity landscape, Security Operations Centers (SOCs) face an unprecedented challenge: alert fatigue. This phenomenon, characterized by the overwhelming volume of security alerts that desensitize analysts and compromise their effectiveness, has become a critical concern for organizations nationwide. As cyber threats continue to escalate, with Microsoft in “Microsoft Digital Defense Report: 600 million cyberattacks per day around the globe”1 reporting that their customers face an astounding 600 million attacks daily, the need for effective alert prioritization strategies has never been more urgent.
Alert fatigue occurs when security professionals become overwhelmed by the sheer volume of alerts generated by their security infrastructure, leading to decreased responsiveness, missed threats, and ultimately, compromised security posture. This article explores the depth of the alert fatigue problem, its impact on Australian organizations, and evidence-based strategies for effective prioritization that can help cybersecurity teams maintain vigilance without sacrificing their well-being or operational effectiveness.
Understanding Alert Fatigue: The Scale of the Problem
The magnitude of alert fatigue in modern cybersecurity operations is staggering. According to peer-reviewed research published in Association for Computing Machinery’s ACM Computing Surveys “Alert Fatigue in Security Operations Centres: Research Challenges and Opportunities,”2 it was found that 51% of SOC teams are overwhelmed with alert volume, while according IBM as reported in the same Association for Computing Machinery’s ACM Computing Surveys above, that teams were only able to resolve 49% of alerts assigned to them in a workday. These statistics paint a concerning picture of an industry struggling to keep pace with the demands of modern threat detection.
The Australian cybersecurity landscape reflects these global trends. Many Australian security professionals receive significant amount of cloud security alerts per day. This deluge of information creates a paradox: while organizations invest heavily in security tools to enhance protection, these same tools generate massive volumes of events and alerts that can overwhelm their human operators.
The proliferation of security tools contributes significantly to this challenge. Microsoft’s “How Microsoft Security partners are helping customers do more with less“3 reports 78 percent of CISOs report having 16 or more security tools, and many seek to consolidate.cThis fragmented security ecosystem creates multiple streams of alerts, each with different formats, severity levels, and contextual information, making it increasingly difficult for analysts to prioritize and respond effectively.
The Human Cost of Alert Fatigue
Beyond the technical challenges, alert fatigue exacts a significant toll on cybersecurity professionals. Studies demonstrate that after hours of sifting through thousands of alerts, accuracy and attention drop sharply.
A high number of IT security professionals ignore alerts due to the prevalence of false positives. This selective attention, while a natural human response to information overload, creates dangerous blind spots where critical threats can be overlooked. The result is a weakened security posture precisely when organizations need it most.
Post-pandemic research by the US National Library of Medicine and National Center for Biotechnology Information in “A deeper look into cybersecurity issues in the wake of Covid-19: A survey”4 indicates that the problem has intensified, with increased percentage of security operations teams reporting higher alert volumes compared to pre-pandemic levels. This increase, combined with the shift to remote work and expanded attack surfaces, has created a perfect storm for alert fatigue in Australian organizations.
The Business Impact of Alert Fatigue
The consequences of alert fatigue extend far beyond overwhelmed analysts. According to IBM’s Cost of a Data Breach Report 20245, 4.9M was the global average cost of a data breach in 2024: a 10% increase over last year and the highest total ever, with an average time to identify and contain a breach of 258 days. Detection time represents the most significant contributor to overall breach costs, making effective alert prioritization a critical business imperative.
Organizations using more than 50 security tools show measurable performance degradation. An IBM study analysed in “IBM Study: Security Response Planning on the Rise, But Containing Attacks Remains an Issue,”6 indicates that these organizations rank themselves 8% lower in their ability to detect attacks and approximately 7% lower in their capability to respond to incidents. This finding suggests that the complexity introduced by multiple security tools can actually diminish overall security effectiveness.
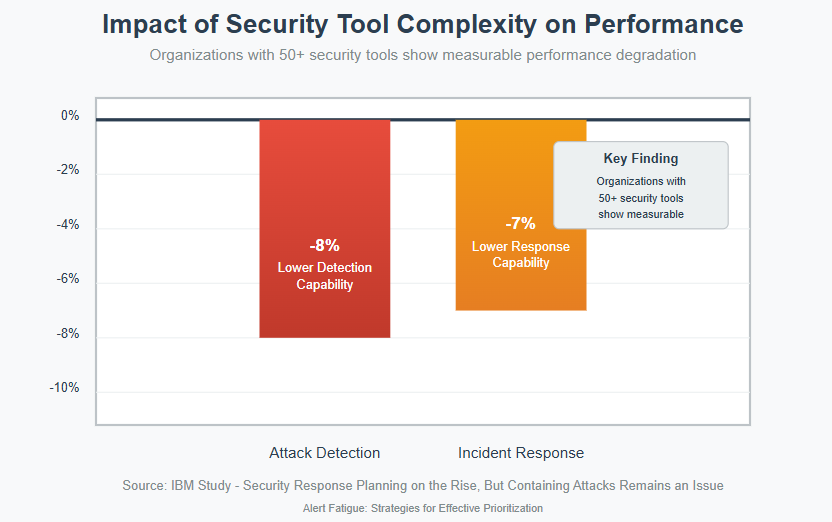
For Australian organizations, these statistics represent not just an operational challenge but a competitive disadvantage in an increasingly digital economy.
Six Evidence-Based Strategies for Effective Alert Prioritization
1. Leveraging Threat Intelligence for Contextual Prioritization
Microsoft’s approach to combating alert fatigue begins with comprehensive threat intelligence. By amalgamating trillions of daily signals across all clouds and platforms, organizations can develop a holistic view of the global security ecosystem. This intelligence-driven approach enables automated actions when threats are detected and provides actionable intelligence to security teams for contextual analysis.
The integration of threat intelligence into alert prioritization systems allows for dynamic scoring based on current threat landscapes. Alerts associated with known threat actor tactics, techniques, and procedures (TTPs) can be automatically elevated, while those related to outdated or low-probability threats can be deprioritized. This approach ensures that analyst attention is directed toward the most relevant and timely threats.
2. Native Integration and Ecosystem Consolidation
The fragmentation of security tools contributes significantly to alert fatigue. Microsoft’s strategy emphasizes native integration across threat protection solution stacks, enabling organizations to connect disparate threat signals and develop comprehensive incident contexts. This approach involves grouping quality alerts from different environment components and stitching together threat elements to create coherent narratives.
First-party security solutions within integrated ecosystems enable real-time interactions among tools, backed by insights from intelligent security graphs. This integration improves alert quality, significantly reduces false positives at the source, and in some cases, enables automatic remediation at the threat protection level. Organizations implementing this strategy report substantial reductions in alert volume without compromising detection capabilities.
3. Machine Learning for Intelligent Alert Correlation
Advanced machine learning represents one of the most promising approaches to alert fatigue reduction. As explained in “Advanced multistage attack detection in Microsoft Sentinel,”7 Microsoft’s Azure Sentinel employs three key machine learning pillars: Fusion technology, built-in machine learning, and “bring your own machine learning” capabilities. The Fusion technology uses scalable learning algorithms to correlate millions of lower fidelity anomalous activities into tens of high-fidelity incidents.
This approach enables automatic detection of multistage attacks by identifying combinations of anomalous behaviors and suspicious activities observed at various stages of the kill chain. Organizations implementing machine learning-based alert correlation report significant reductions in signal noise while maintaining or improving detection accuracy.
4. Watchlists and Allow Lists for Precision Filtering
Watchlists ensure that alerts containing specific entities are promoted through higher severity assignment or selective alerting. This capability serves multiple functions in alert prioritization, including the creation of “allow” lists to suppress alerts from users or devices performing tasks that would normally trigger alerts, thereby preventing benign events from becoming alerts.
The implementation of watchlists requires careful consideration of organizational workflows and legitimate activities that might trigger security alerts. Regular review and updates of these lists ensure they remain relevant and effective in reducing false positives while maintaining security coverage.
5. User and Entity Behavior Analytics (UEBA) for Context-Aware Prioritization
UEBA capabilities target use cases such as abuse of privileged identities, compromised entities, data exfiltration, and insider threat detection. By analyzing logs and alerts from connected data sources, UEBA systems build baseline behavioral profiles of organizational entities across peer groups and time horizons.
This behavioral context enables SOC analysts to reduce both false positives and false negatives by automatically leveraging contextual and behavioral information that traditional alert rules typically lack. The result is more accurate threat detection and prioritization based on deviation from established behavioral norms.
6. Automation and Orchestration for Routine Task Management
The lower tiers of SOC operations typically handle alert triage, where critical decisions determine whether alerts warrant further investigation. Automation of well-known tasks that don’t require human judgment can significantly impact alert noise reduction. Organizations can leverage automation platforms to build playbooks that automate tasks of varying complexity.
Real-time automation enables response teams to reduce their workload by fully automating routine responses to recurring alert types. This allows SOC teams to concentrate on unique alerts, pattern analysis, and proactive threat hunting activities. Automated remediation capabilities can include IP blocking, account disabling, and ticket creation, freeing analysts for higher-value activities.
Implementation Considerations for Australian Organizations
Regulatory Compliance and Privacy
Australian organizations must consider compliance requirements when implementing alert prioritization strategies. The Australian Privacy Principles and sector-specific regulations may impact how organizations collect, analyze, and retain security data. The Australian Cyber Security Centre (ACSC) provides guidance on balancing security effectiveness with privacy requirements.
Skills and Resource Allocation
The Australian cybersecurity skills shortage, as documented in the ACSC’s releases, affects implementation of sophisticated alert prioritization strategies. Organizations must consider their human resource capabilities when selecting and implementing these approaches. Automation and machine learning can help bridge skills gaps, but require initial investment in training and infrastructure.
Integration with Existing Infrastructure
Many Australian organizations operate hybrid IT environments combining on-premises and cloud infrastructure. Alert prioritization strategies must accommodate this complexity while maintaining consistent security coverage. The integration challenges are particularly relevant for organizations undergoing digital transformation initiatives.
Measuring Success: Key Performance Indicators
Alert Volume Reduction
Organizations should track the reduction in alert volume following implementation of prioritization strategies. Successful implementations typically achieve 30-70% reduction in alert volume while maintaining or improving detection capabilities.
Mean Time to Detection (MTTD) and Response (MTTR)
These metrics indicate the effectiveness of prioritization strategies in enabling faster threat identification and response. Organizations should establish baselines before implementation and track improvements over time.
False Positive Rates
The percentage of alerts that prove to be false positives should decrease as prioritization strategies mature. Organizations should aim for false positive rates below 10% for high-priority alerts.
Analyst Satisfaction and Retention
Given the human cost of alert fatigue, organizations should track analyst satisfaction scores and retention rates as indicators of strategy effectiveness. Improved job satisfaction often correlates with better security outcomes.
Future Considerations and Emerging Trends
Artificial Intelligence and Advanced Analytics
The evolution of AI capabilities promises further improvements in alert prioritization. Natural language processing and advanced pattern recognition will enable more sophisticated analysis of alert content and context.
Threat Intelligence Sharing
Collaborative threat intelligence sharing, as promoted by the ACSC in “Join the Cyber Threat Intelligence Sharing service through Sentinel,“8 will enhance the effectiveness of prioritization strategies by providing broader context for threat assessment.
Zero Trust Architecture
The adoption of zero trust principles will influence alert prioritization by changing the nature of security events and the context in which they occur.
Conclusion
Alert fatigue represents a critical challenge for Australian cybersecurity operations, but it is not insurmountable. The six evidence-based strategies outlined in this article provide a comprehensive framework for addressing this challenge through intelligent prioritization, automation, and integration. Organizations that successfully implement these strategies report significant improvements in operational efficiency, threat detection capabilities, and analyst satisfaction.
The key to success lies in adopting a holistic approach that combines technology solutions with process improvements and human factors considerations. As the threat landscape continues to evolve, organizations must remain agile in their approach to alert prioritization, continuously refining their strategies based on emerging threats and technological capabilities.
By addressing alert fatigue proactively, Australian organizations can maintain robust security postures while preserving the well-being and effectiveness of their cybersecurity teams. The investment in sophisticated alert prioritization strategies will pay dividends in improved security outcomes, reduced operational costs, and enhanced organizational resilience.
References
- Microsoft. (2024). Microsoft Digital Defense Report: 600 Million Cyberattacks Per Day Around The Globe. https://news.microsoft.com/en-cee/2024/11/29/microsoft-digital-defense-report-600-million-cyberattacks-per-day-around-the-globe/ ↩︎
- Shahroz, T., et al. (2025). Alert Fatigue in Security Operations Centres: Research Challenges and Opportunities. ACM Computing Surveys. https://dl.acm.org/doi/full/10.1145/3723158 ↩︎
- Vasu J. (2022). How Microsoft Security Partners Are Helping Customers Do More With Less. Microsoft. https://www.microsoft.com/en-us/security/blog/2022/07/19/how-microsoft-security-partners-are-helping-customers-do-more-with-less/ ↩︎
- Moatsum, A., et al. (2022). A Deeper Look Into Cybersecurity Issues In The Wake Of Covid-19: A Survey. National Library of Medicine. https://pmc.ncbi.nlm.nih.gov/articles/PMC9367180/ ↩︎
- IBM. (2024). Cost of a Data Breach Report 2024. https://www.ibm.com/reports/data-breach ↩︎
- IBM. (2020). Ibm Study: Security Response Planning On The Rise, But Containing Attacks Remains An Issue. https://newsroom.ibm.com/2020-06-30-IBM-Study-Security-Response-Planning-on-the-Rise-But-Containing-Attacks-Remains-an-Issue ↩︎
- Microsoft. (2024). Advanced Multistage Attack Detection In Microsoft Sentinel. https://learn.microsoft.com/en-us/azure/sentinel/fusion ↩︎
- Australian Cyber Security Centre (ACSC). (2024). Join The Cyber Threat Intelligence Sharing Service Through Sentinel. Australian Signals Directorate (ASD). https://www.cyber.gov.au/about-us/view-all-content/news-and-media/join-the-cyber-threat-intelligence-sharing-service-through-sentinel ↩︎
At Christian Sajere Cybersecurity and IT Infrastructure, we understand the critical challenge of alert fatigue facing Australian organizations. Our intelligent prioritization solutions leverage advanced analytics and automation to cut through the noise, enabling your security team to focus on what matters most. Let us help you transform alert overload into strategic advantage.
Related Blog Posts
- Data-Centric Security Architecture: Building Resilience Through Data-Focused Protection
- Network Security Zoning and Segmentation Design: Building Resilient Digital Perimeters in 2025
- Threat Intelligence Sharing: Communities and Frameworks
- Healthcare Information Security: Australian Privacy Requirements
- Cost-Effective Security Solutions for Limited Budgets
- Threat Hunting: Methodologies and Tools
- Email Data Loss Prevention Strategies: A Comprehensive Guide for Australian Organizations


