In today’s rapidly evolving digital landscape, Australian businesses are increasingly turning to cloud solutions to drive innovation, scalability, and operational efficiency. In Q3 FY 2024 (ended March 31, 2024), Microsoft reported in its Microsoft Q3 FY 2024 Earnings Release1, a 31 percent year-over-year increase in revenue from Azure and other cloud services, contributing to a 24 percent overall growth in its server products and cloud services segment. However, with this digital transformation comes the critical responsibility of maintaining robust cybersecurity practices that align with Australian regulatory requirements and industry best practices.
The Australian cybersecurity landscape presents unique challenges and opportunities. According to the Australian Cyber Security Centre’s (ACSC) Annual Cyber Threat Report 2023–242, cyber threats continue to evolve in sophistication and frequency, making comprehensive cloud security strategies more crucial than ever. This article explores essential Azure security best practices specifically tailored for Australian businesses, drawing insights from Microsoft’s latest security frameworks, ACSC guidelines, and industry-leading research.
Understanding the Australian Cloud Security Landscape
Current Market Dynamics
Microsoft Azure’s growth trajectory in Australia has been remarkable, with the platform experiencing 33% revenue growth in Q1 FY2025 globally, as reported in Microsoft Q1 FY2025 Earnings Release3. Interestingly, Australian users demonstrate a good desire for accessing Azure via mobile devices. This mobile-first approach necessitates additional security considerations for Australian organizations.
The Australian government’s commitment to cloud security is evident through initiatives like the 2024 Azure, Dynamics 365, and Microsoft 365 Information Security Registered Assessors Program (IRAP)4 assessments, which evaluate Microsoft’s cloud platforms against the ACSC’s Cloud Assessment and Authorisation Framework5. These assessments provide Australian organizations with the confidence and compliance foundation necessary for secure cloud adoption.
Threat Landscape Insights
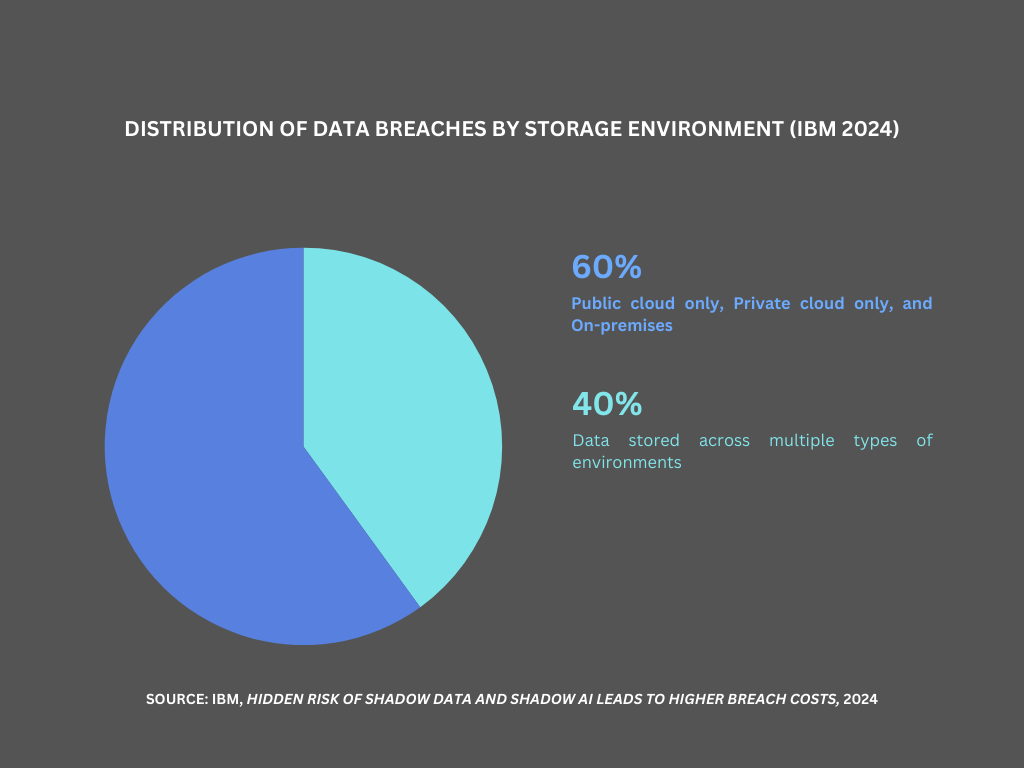
Recent data from IBM’s Hidden risk of shadow data and shadow AI leads to higher breach costs6 reveals that 40% of all data breaches involve data distributed across multiple environments, with breached data stored in public clouds incurring the high breach costs. For Australian businesses, this underscores the critical importance of implementing comprehensive cloud security strategies that address multi-environment challenges.
The ACSC’s Annual Cyber Threat Report 2023-2024 highlights real-world security incidents, including a case where unauthorized access to a hospital’s network occurred through a Microsoft Azure Virtual Desktop (AVD) accessed via an employee’s personal device. Such incidents emphasize the need for robust access controls and device management policies.
Core Azure Security Best Practices
1. Identity and Access Management (IAM) Excellence
Multi-Factor Authentication (MFA) Implementation
Multi-factor authentication stands as the most critical security control for cloud environments. According to IBM’s X-Force Threat Intelligence Index as referenced in “IBM Report: Cybercriminals Intensify Attacks on User Identities in the UK, Complicating Recovery Efforts for Enterprises”7, 85 percent of cyberattacks targeting critical infrastructure sectors could have been prevented through the proper implementation of basic security controls, including multi-factor authentication (MFA), timely patching, and least-privilege access principles. While precise adoption figures vary, industry trends show growing use of MFA and biometric authentication as organizations strengthen identity and access management strategies.
Best Practices for Australian Businesses:
- Enable MFA for all Azure Active Directory (now Microsoft Entra ID) accounts
- Implement conditional access policies based on user location, device compliance, and risk assessment
- Utilize Azure AD Privileged Identity Management (PIM) for administrative accounts
- Regularly review and audit access permissions
Azure AD Integration with ACSC Guidelines
The ACSC’s Essential Eight security8 practices emphasize strong authentication mechanisms. Australian businesses should align their Azure AD configurations with these guidelines by:
- Implementing strong password policies that exceed basic complexity requirements
- Enabling password protection features to prevent common and breached passwords
- Configuring sign-in risk policies to automatically respond to suspicious activities
2. Network Security and Segmentation
Azure Network Security Groups and Application Security Groups
Proper network segmentation is fundamental to limiting the blast radius of potential security incidents. The ACSC specifically in “Guidelines for Networking”9 (part of the Information Security Manual)10 recommends network segmentation as part of comprehensive cybersecurity strategies.
Implementation Strategies:
- Deploy Azure Firewall for centralized network security policy enforcement
- Utilize Azure DDoS Protection Standard for critical workloads
- Implement Virtual Network (VNet) peering with careful access controls
- Configure Network Security Groups (NSGs) with deny-by-default policies
Server Application Hardening
Following ACSC guidelines for server application hardening, Australian businesses should focus on:
- Securing internet-accessible web applications through input sanitization
- Implementing TLS (not SSL) for all communications
- Hardening databases, especially those containing sensitive data
- Regular security assessments of applications accessing high-value data
3. Data Protection and Encryption
Azure Key Vault and Encryption Services
Data protection remains paramount for Australian businesses, particularly those handling personal information subject to Privacy Act requirements.
Key Implementation Areas:
- Utilize Azure Key Vault for centralized key management
- Implement Azure Disk Encryption for virtual machine storage
- Enable Azure Storage Service Encryption for data at rest
- Use Azure Information Protection for data classification and protection
Backup and Disaster Recovery
The importance of robust backup strategies cannot be overstated, with the ACSC emphasizing data backup as a critical component of cyber resilience:
- Implement Azure Backup for virtual machines and databases
- Configure geo-redundant storage for critical data
- Regularly test backup restoration procedures
- Maintain offline backup copies following the 3-2-1 backup rule
4. Monitoring and Threat Detection
Azure Security Center and Azure Sentinel
Continuous monitoring forms a cornerstone of effective cloud security. The Commonwealth Cyber Security Posture in 202411 report indicates that 89% of entities now have centralized logging capabilities, highlighting the widespread recognition of monitoring importance.
Monitoring Best Practices:
- Deploy Azure Security Center for continuous security assessment
- Implement Azure Sentinel for Security Information and Event Management (SIEM)
- Configure Azure Monitor for comprehensive infrastructure monitoring
- Establish automated incident response procedures
ACSC Threat Intelligence Integration
Australian businesses can leverage the ACSC’s Cyber Threat Intelligence Sharing (CTIS) program through dedicated Azure Marketplace solutions. This integration enables organizations to:
- Share threat indicators with the ACSC
- Receive real-time threat intelligence updates
- Enhance their security posture through collaborative defense mechanisms
Advanced Security Configurations
5. Compliance and Governance
Azure Policy and Blueprints
Maintaining compliance with Australian regulations requires systematic governance approaches:
- Implement Azure Policy for automated compliance monitoring
- Utilize Azure Blueprints for consistent environment deployment
- Regular compliance assessments against Australian Privacy Principles
- Documentation of security controls and procedures
IRAP Assessment Preparation
For organizations requiring government-grade security assurance:
- Understand IRAP assessment requirements and timelines
- Prepare documentation for security control implementation
- Engage with IRAP assessors early in the planning process
- Maintain ongoing compliance monitoring
6. Application Security
Secure Development Practices
Following the principle of “secure by design” emphasized by the ACSC and international partners:
- Implement Azure DevSecOps practices
- Utilize Azure Security Center recommendations for applications
- Regular security code reviews and vulnerability assessments
- Container security for Azure Kubernetes Service deployments
Email Security Enhancement
The ACSC in “Guidelines for email“12 specifically recommends email security measures that can be implemented through Azure:
- Deploy Sender Policy Framework (SPF) with ‘hard fail’ configurations
- Implement DMARC DNS records to prevent domain spoofing
- While the ACSC does not endorse specific products, Microsoft recommends utilizing Microsoft Defender for Office 365 for advanced threat protection in alignment with these controls
Emerging Threats and Future Considerations
AI and Machine Learning Security
Australian businesses should consider:
- Secure AI model deployment and management
- Data privacy in machine learning workflows
- Adversarial attack protection for AI systems
- Responsible AI practices aligned with emerging Australian AI ethics frameworks
Credential Theft and Infostealer Threats
Recent IBM research in “X-Force Threat Intelligence Index 2024 reveals stolen credentials as top risk, with AI attacks on the horizon”13 shows a 71% year-over-year increase in credential-based attacks, with an 84% increase in infostealers delivered via phishing as seen in the 2025 X‑Force Threat Intelligence Index14. Australian businesses should:
- Implement Zero Trust architecture principles
- Utilize Azure AD Identity Protection for risk-based authentication
- Regular security awareness training for employees
- Endpoint detection and response integration with Azure Sentinel
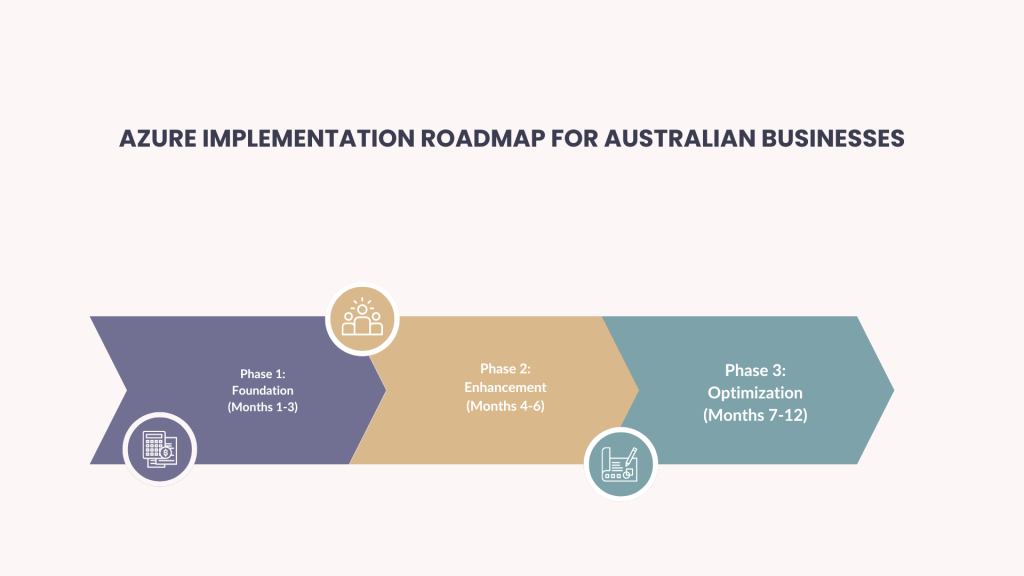
Implementation Roadmap for Australian Businesses
Phase 1: Foundation (Months 1-3)
- Enable MFA across all Azure services
- Implement basic network security groups
- Deploy Azure Security Center
- Establish backup procedures
Phase 2: Enhancement (Months 4-6)
- Configure Azure Sentinel for SIEM capabilities
- Implement conditional access policies
- Deploy Azure Key Vault for key management
- Establish incident response procedures
Phase 3: Optimization (Months 7-12)
- IRAP assessment preparation (if required)
- Advanced threat protection deployment
- Zero Trust architecture implementation
- Continuous improvement processes
Cost Considerations and ROI
The skills shortage in cybersecurity continues to impact Australian businesses, with IBM research indicating an additional USD 1.76 million cost in data breach aftermath due to staffing challenges as it stated in “The cybersecurity skills gap contributed to a USD 1.76 million increase in average breach costs”15. Implementing proper Azure security practices can help mitigate these costs through:
- Automated security monitoring and response
- Reduced manual security management overhead
- Prevention of costly data breaches
- Improved compliance posture reducing regulatory risks
Conclusion
Azure security best practices for Australian businesses require a comprehensive approach that balances innovation with robust security controls. By aligning with ACSC guidelines, implementing proven security frameworks, and maintaining continuous monitoring and improvement processes, organizations can harness the full potential of cloud technologies while maintaining strong security postures.
The evolving threat landscape demands proactive security strategies that go beyond basic implementations. Australian businesses that invest in comprehensive Azure security practices today will be better positioned to handle future challenges while maintaining the trust of their customers and stakeholders.
Success in cloud security requires ongoing commitment, regular assessment, and adaptation to emerging threats. By following the practices outlined in this guide and maintaining alignment with Australian cybersecurity frameworks, organizations can achieve both security excellence and business agility in their cloud journey.
References and Sources
- Microsoft, “Microsoft Q3 FY2024 Earnings Release”, 2024 https://www.microsoft.com/en-us/investor/earnings/fy-2024-q3/press-release-webcast ↩︎
- Australian Cyber Security Centre’s (ACSC), “Annual Cyber Threat Report 2023–24” https://www.cyber.gov.au/about-us/view-all-content/reports-and-statistics/annual-cyber-threat-report-2023-2024 ↩︎
- Microsoft, “Microsoft Q1 FY2025 Earnings Release”, 2025 https://www.microsoft.com/en-us/investor/earnings/fy-2025-q1/press-release-webcast ↩︎
- Microsoft, “Information Security Registered Assessors Program (IRAP)”, 2024 https://learn.microsoft.com/en-us/compliance/regulatory/offering-irap-australia ↩︎
- Australian Cyber Security Centre (ACSC), “Cloud Assessment and Authorisation Framework”, 2024 https://www.cyber.gov.au/resources-business-and-government/maintaining-devices-and-systems/cloud-security-guidance/cloud-assessment-and-authorisation ↩︎
- IBM, “Hidden risk of shadow data and shadow AI leads to higher breach costs”, https://www.ibm.com/think/insights/hidden-risk-shadow-data-ai-higher-costs? ↩︎
- IBM, IBM’s X-Force Threat Intelligence Index; “IBM Report: Cybercriminals Intensify Attacks on User Identities in the UK, Complicating Recovery Efforts for Enterprises”, 2024 https://uk.newsroom.ibm.com/IBM-Report-Cybercriminals-Intensify-Attacks-on-User-Identities-in-the-UK-Complicating-Recovery-Efforts-for-Enterprises ↩︎
- Australian Cyber Security Centre (ACSC), “Essential Eight security”, https://www.cyber.gov.au/resources-business-and-government/essential-cybersecurity/essential-eight ↩︎
- Australian Cyber Security Centre “ACSC), “Guidelines for Networking”, 2025 https://www.cyber.gov.au/resources-business-and-government/essential-cybersecurity/ism/cybersecurity-guidelines/guidelines-networking ↩︎
- Australian Cyber Security Centre (ACSC), “Information Security Manual”, 2025 https://www.cyber.gov.au/resources-business-and-government/essential-cybersecurity/ism ↩︎
- Australian Signals Directorate (ASD), “Commonwealth Cyber Security Posture in 2024”, 2024 https://www.cyber.gov.au/about-us/view-all-content/reports-and-statistics/commonwealth-cyber-security-posture-2024 ↩︎
- Australian Cyber Security Centre (ACSC), “Guidelines for email“, 2025 https://www.cyber.gov.au/resources-business-and-government/essential-cybersecurity/ism/cybersecurity-guidelines/guidelines-email ↩︎
- IBM, “X-Force Threat Intelligence Index 2024 reveals stolen credentials as top risk, with AI attacks on the horizon”, 2024 https://www.ibm.com/think/x-force/2024-x-force-threat-intelligence-index ↩︎
- IBM, “2025 X‑Force Threat Intelligence Index”, https://www.ibm.com/thought-leadership/institute-business-value/en-us/report/2025-threat-intelligence-index ↩︎
- IBM, “The cybersecurity skills gap contributed to a USD 1.76 million increase in average breach costs”, 2024 https://www.ibm.com/think/insights/cybersecurity-skills-gap-contributed-increase-average-breach-costs ↩︎
At Christian Sajere Cybersecurity and IT Infrastructure, we understand the complexities of Azure security implementation for Australian businesses. Our specialized expertise in cloud security architecture and ACSC compliance helps organizations build robust, scalable security frameworks. Let us guide your Azure security transformation.
Related Blog Posts
- Hash Functions and Their Applications in Security
- PCI DSS: Implementation Guide for Australian Merchants
- Managed Security Services: When to Outsource
- Security Architecture Review Processes: A Comprehensive Guide to Modern Cybersecurity Assessment
- Public Key Infrastructure (PKI) Design and Management: A Comprehensive Guide for Modern Organizations
- APRA CPS 234: Compliance Guide for Financial Institutions
- SOC 2 Compliance: Preparation and Audit Process


