In today’s rapidly evolving digital landscape, organizations face an unprecedented challenge: ensuring their cybersecurity investments directly support and enhance their business objectives. The practice of mapping security controls to business requirements has emerged as a critical discipline that bridges the gap between technical security measures and strategic business outcomes. This comprehensive analysis explores how organizations can effectively align their cybersecurity frameworks with core business needs, drawing from industry best practices and authoritative guidance from leading technology companies and government agencies.
The cybersecurity landscape has fundamentally shifted from a purely technical discipline to a strategic business enabler. Organizations can no longer afford to implement security measures in isolation; every control must be justified, measured, and aligned with specific business requirements. This alignment ensures that cybersecurity investments not only protect assets but also enable business growth, compliance, and competitive advantage.
The challenge lies in creating a systematic approach that translates abstract business objectives into concrete security controls while maintaining flexibility for emerging threats and changing business conditions. This article examines proven methodologies for achieving this alignment, supported by empirical data and industry frameworks.
The Business Case for Security-Business Alignment
Financial Impact and ROI
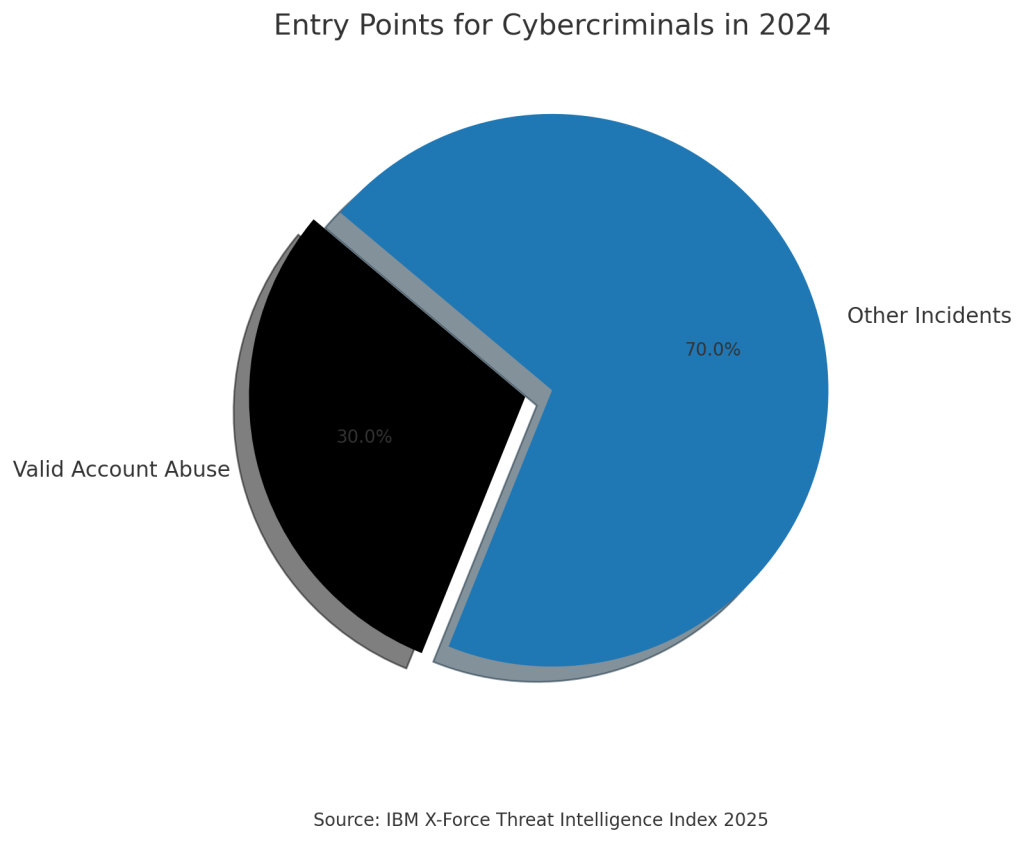
Recent industry data reveals the stark financial implications of misaligned cybersecurity investments. According to IBM’s 2025 X‑Force Threat Intelligence Index1, organizations that align their security controls with business objectives tend to experience lower incident response costs and faster recovery times. Conversely, when security efforts are misaligned—resulting in fragmented response efforts, breach-related downtime and financial impact are significantly greater. Abusing valid accounts remained the preferred entry point into victim environments for cybercriminals in 2024, representing 30% of all incidents X-Force responded to as seen in IBM’s 2025 X‑Force Threat Intelligence Index2, highlighting the critical importance of identity and access management controls aligned with business user workflows.
The cost of cybersecurity incidents extends beyond immediate financial losses. Organizations must consider:
Direct Financial Losses: Immediate costs associated with incident response, system recovery, and regulatory fines
- Operational Disruption: Business process interruption and productivity losses
- Reputational Damage: Long-term impact on customer trust and market position
- Compliance Costs: Ongoing expenses related to regulatory adherence and audit requirements
Regulatory Compliance and Business Operations
Regulatory frameworks increasingly demand that organizations demonstrate not just technical security measures, but also their business justification and effectiveness. The Australian Cyber Security Centre’s Information Security Manual (ISM)3 provides a comprehensive framework that organizations can apply using their risk management framework to protect their systems and data. The Information security manual (ISM) is a cybersecurity framework that an organisation can apply, using their risk management framework, to protect their information technology and operational technology systems, applications and data from cyberthreats.
This regulatory emphasis on business alignment reflects a broader understanding that effective cybersecurity cannot exist in a vacuum but must be integrated into the fabric of business operations.
Framework-Based Approaches to Security-Business Alignment
Microsoft’s Governance and Risk Management Model
Microsoft’s approach to security governance provides a valuable blueprint for organizations seeking to align security controls with business requirements. The MSP, as explained in “Governance, risk, and compliance overview”4, organizes Microsoft’s security policies, standards, and requirements so they can be implemented across all Microsoft engineering groups and business units. Individual business units are responsible for specific implementations of Microsoft security policies.
This model demonstrates several key principles:
- Centralized Policy with Distributed Implementation: Core security policies are developed centrally but implemented in ways that align with specific business unit requirements
- Continuous Alignment: Security policies are regularly updated to account for new technologies, regulatory requirements, and business changes
- Risk-Based Prioritization: Controls are prioritized based on their alignment with business risk tolerance and objectives
Australian Cyber Security Centre’s Essential Eight
The ACSC’s Essential Eight framework5 represents a business-focused approach to cybersecurity that prioritizes controls based on their effectiveness in protecting business operations. While no set of mitigation strategies are guaranteed to protect against all cyberthreats, organisations are recommended to implement eight essential mitigation strategies from the Strategies to mitigate cybersecurity incidents as a baseline.
The Essential Eight framework’s strength lies in its practical approach to business alignment:
- Application Control: Ensuring only approved applications run, directly supporting business productivity while maintaining security
- Patch Management: Balancing security updates with business continuity requirements
- User Access Controls: Implementing least-privilege principles aligned with business role requirements
- Network Segmentation: Protecting critical business systems while enabling necessary connectivity
Industry-Specific Alignment Strategies
Different industries require unique approaches to security-business alignment:
Financial Services: Emphasis on transaction security, customer data protection, and regulatory compliance controls that enable digital banking services while maintaining trust.
Healthcare: Integration of security controls with patient care workflows, ensuring HIPAA compliance while enabling telemedicine and digital health initiatives.
Manufacturing: Balancing operational technology security with production efficiency, implementing controls that protect industrial systems without disrupting manufacturing processes.
Government: Aligning security measures with public service delivery requirements while maintaining citizen privacy and national security considerations.
Practical Implementation Strategies
Business Requirements Assessment
The foundation of effective security-business alignment begins with a comprehensive assessment of business requirements. This process involves:
- Stakeholder Engagement: Systematic consultation with business leaders, process owners, and end-users to understand operational requirements
- Risk Identification: Cataloging business risks that can be mitigated through security controls
- Performance Metrics: Establishing measurable criteria for security control effectiveness from a business perspective
- Compliance Mapping: Identifying regulatory and contractual requirements that impact business operations
Control Selection and Prioritization
Once business requirements are established, organizations must select and prioritize security controls based on their alignment with these requirements. This process involves:
- Business Impact Analysis: Evaluating how each potential security control affects business operations, considering both protective benefits and operational overhead.
- Cost-Benefit Analysis: Comparing the cost of implementing controls against the business value they provide, including risk reduction and compliance benefits.
- Implementation Feasibility: Assessing the organization’s capability to implement and maintain controls while meeting business requirements.
Technology Integration and Automation
Modern security-business alignment increasingly relies on technology platforms that can adapt controls to changing business requirements. Microsoft’s approach to cloud security demonstrates this principle, where security controls are embedded into business applications and workflows rather than operating as separate systems.
The integration of artificial intelligence and machine learning into security operations enables dynamic alignment between security controls and business requirements. These technologies can automatically adjust security parameters based on business context, user behavior, and risk levels.
Measuring Success: Metrics and KPIs
Business-Aligned Security Metrics
Traditional security metrics often fail to communicate value in business terms. Organizations must develop metrics that demonstrate how security controls support business objectives:
Business Continuity Metrics:
- Reduction in business-critical system downtime
- Improvement in incident recovery times
- Maintenance of service level agreements during security incidents
Operational Efficiency Metrics:
- Reduction in security-related business process delays
- Improvement in user productivity despite security controls
- Decrease in security-related help desk tickets
Compliance and Risk Metrics:
- Achievement of regulatory compliance targets
- Reduction in audit findings and remediation costs
- Improvement in risk assessment scores
Continuous Monitoring and Adaptation
Effective security-business alignment requires ongoing monitoring and adaptation. Organizations must establish processes for:
- Regular Alignment Reviews: Periodic assessment of whether security controls continue to support business requirements
- Business Change Management: Procedures for updating security controls when business requirements change
- Threat Landscape Monitoring: Continuous evaluation of emerging threats and their potential business impact
- Performance Optimization: Ongoing refinement of security controls to improve business alignment
Emerging Trends and Future Considerations
Artificial Intelligence and Machine Learning
The integration of AI and ML technologies is transforming how organizations align security controls with business requirements, as can be seen in Google’s Secure AI Framework (SAIF)6.
. These technologies enable:
- Dynamic Risk Assessment: Real-time evaluation of security risks based on business context and user behavior
- Automated Control Adjustment: Automatic modification of security parameters based on changing business requirementsPredictive Security: Anticipation of security needs based on business trends and threat intelligence
Zero Trust Architecture
Zero Trust principles are revolutionizing security-business alignment by embedding security controls directly into business processes and workflows. This approach ensures that security becomes an enabler rather than an impediment to business operations.
Quantum Computing Implications
The risk quantum computing poses to modern standards of public-key encryption will become unavoidable in the future. Organizations must begin preparing for post-quantum cryptography implementations that align with long-term business strategies as emphasized in the National Institute of Standards and Technology’s “NIST Releases First 3 Finalized Post-Quantum Encryption Standards.”7
Industry Case Studies
Case Study 1: Financial Services Organization
A major Australian bank successfully aligned its security controls with business requirements by implementing a risk-based approach that prioritized customer experience while maintaining regulatory compliance. The organization:
- Implemented adaptive authentication that adjusted security requirements based on transaction risk and customer behavior
- Deployed security controls that enabled digital banking services while protecting customer data
- Established metrics that measured both security effectiveness and customer satisfaction
Results: 40% reduction in security-related customer complaints, 25% improvement in digital banking adoption rates, and 100% compliance with regulatory requirements.
Case Study 2: Healthcare Provider
A regional healthcare network aligned its security controls with patient care requirements by:
- Implementing role-based access controls that matched clinical workflows
- Deploying security monitoring that protected patient data without disrupting care delivery
- Establishing incident response procedures that prioritized patient safety
Results: 60% reduction in security-related delays in patient care, 30% improvement in clinician satisfaction with IT systems, and zero patient data breaches.
Case Study 3: Manufacturing Company
A global manufacturing company aligned its cybersecurity controls with operational technology requirements by:
- Implementing network segmentation that protected critical systems while enabling necessary connectivity
- Deploying security controls that considered production schedules and maintenance windows
- Establishing security monitoring that detected threats without interfering with manufacturing processes
Results: 50% reduction in security-related production delays, 35% improvement in operational technology reliability, and comprehensive protection against industrial cyber threats.
Best Practices and Recommendations
Organizational Alignment
- Executive Sponsorship: Ensure senior leadership understands and champions security-business alignment initiatives
- Cross-Functional Teams: Establish teams that include both security and business representatives
- Communication Strategies: Develop clear communication channels between security and business units
- Training and Awareness: Provide training that helps business users understand security requirements in their context
Technical Implementation
- Phased Approach: Implement security controls in phases that align with business priorities and capabilities
- Pilot Programs: Test security controls in limited environments before full deployment
- Integration Planning: Ensure security controls integrate seamlessly with existing business systems
- Monitoring and Alerting: Implement monitoring that provides both security and business-relevant insights
Governance and Oversight
- Policy Development: Create policies that explicitly address security-business alignment requirements
- Regular Reviews: Establish periodic review cycles for security-business alignment
- Change Management: Implement processes for managing changes to security controls based on business requirements
- Risk Management: Integrate security-business alignment into overall risk management frameworks
Challenges and Solutions
Common Implementation Challenges
Resource Constraints: Organizations often lack the resources to implement comprehensive security-business alignment initiatives.
Solution: Prioritize alignment efforts based on business criticality and risk levels, implementing changes incrementally.
Cultural Resistance: Business units may resist security controls that appear to hinder operations.
Solution: Engage stakeholders early in the process and demonstrate how security controls can enable rather than impede business objectives.
Technical Complexity: Modern IT environments can make it difficult to implement aligned security controls.
Solution: Leverage automation and integration platforms that can adapt security controls to business requirements.
Measurement Difficulties: It can be challenging to measure the business value of security controls.
Solution: Develop metrics that connect security outcomes to business objectives and communicate results in business terms.
Conclusion
The alignment of security controls with business requirements represents a fundamental shift in how organizations approach cybersecurity. Rather than viewing security as a necessary overhead, forward-thinking organizations are recognizing security as a strategic enabler that can drive business value while protecting critical assets.
Success in this alignment requires a comprehensive approach that encompasses governance, technology, and culture. Organizations must move beyond traditional security-focused metrics to embrace business-aligned measures of success. They must also be prepared to adapt their approaches as business requirements evolve and new threats emerge.
The frameworks and strategies outlined in this article provide a roadmap for organizations seeking to achieve effective security-business alignment. By following these principles and adapting them to their specific contexts, organizations can create cybersecurity programs that not only protect against threats but also enable business growth and competitive advantage.
The future of cybersecurity lies not in building higher walls, but in creating security controls that seamlessly integrate with and support business objectives. Organizations that master this alignment will be better positioned to thrive in an increasingly digital and interconnected world.
References and Sources
- IBM, “2025 X‑Force Threat Intelligence Index”, 2025 https://www.ibm.com/reports/threat-intelligence ↩︎
- IBM, “2025 X‑Force Threat Intelligence Index”, https://www.ibm.com/reports/threat-intelligence ↩︎
- Australian Cyber Security Centre (ACSC), “Information Security Manual (ISM)”, https://www.cyber.gov.au/resources-business-and-government/essential-cybersecurity/ism ↩︎
- Microsoft, “Governance, risk, and compliance overview”, https://learn.microsoft.com/en-us/compliance/assurance/assurance-governance ↩︎
- Australian Cyber Security Centre (ACSC), “Essential Eight”, https://www.cyber.gov.au/resources-business-and-government/essential-cybersecurity/essential-eight ↩︎
- Google, “Secure AI Framework (SAIF)”, https://safety.google/cybersecurity-advancements/saif/ ↩︎
- National Institute of Standards and Technology (NIST), “NIST Releases First 3 Finalized Post-Quantum Encryption Standards”, https://www.nist.gov/news-events/news/2024/08/nist-releases-first-3-finalized-post-quantum-encryption-standards ↩︎
At Christian Sajere Cybersecurity and IT Infrastructure, we understand that effective cybersecurity isn’t just about protection; it’s about enabling business success. Our specialized approach to mapping security controls to business requirements ensures your organization achieves optimal alignment between security investments and business objectives. Let us help you transform cybersecurity from a cost center into a strategic business enabler.
Contact us today to discover how our tailored security-business alignment strategies can drive your organization’s success.
Related Blog Posts
- Legal Considerations for Penetration Testing in Australia
- Managing Security Debt in Software Development: A Strategic Approach to Long-term Security Excellence
- Adversarial Machine Learning: Understanding the Threats
- Selecting the Right Penetration Testing Partner: A Strategic Guide for Australian Organizations
- Digital Signatures: Implementation and Verification
- Code Review for Security: Techniques and Tools
- Secure Coding Guidelines for Multiple Languages: A Comprehensive Framework for Modern Software Development


